Connection Not Secure After HTTPS SSL Certificate Installation (KBA9293)
KBA
KBA# 9293
Issue
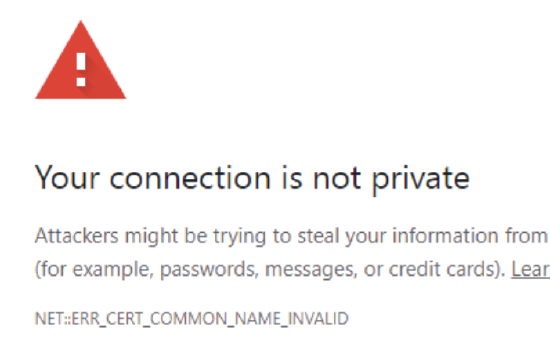
Following installation of SSL certificate for HTTPS connectivity, the connection may still be indicated as "Not Secure" in Chrome or Firefox. The browser error may indicate "ERR_CERT_COMMON_NAME_INVALID"
Applicable Delphix Versions
- Click here to view the versions of the Delphix engine to which this article applies
-
Major Release All Sub Releases 6.0 6.0.0.0, 6.0.1.0, 6.0.1.1, 6.0.2.0, 6.0.2.1, 6.0.3.0, 6.0.3.1, 6.0.4.0, 6.0.4.1, 6.0.4.2, 6.0.5.0, 6.0.6.0, 6.0.6.1, 6.0.7.0, 6.0.8.0, 6.0.8.1, 6.0.9.0, 6.0.10.0, 6.0.10.1, 6.0.11.0, 6.0.12.0, 6.0.12.1, 6.0.13.0, 6.0.13.1, 6.0.14.0
5.3
5.3.0.0, 5.3.0.1, 5.3.0.2, 5.3.0.3, 5.3.1.0, 5.3.1.1, 5.3.1.2, 5.3.2.0, 5.3.3.0, 5.3.3.1, 5.3.4.0, 5.3.5.0, 5.3.6.0, 5.3.7.0, 5.3.7.1, 5.3.8.0, 5.3.8.1, 5.3.9.0 5.2
5.2.2.0, 5.2.2.1, 5.2.3.0, 5.2.4.0, 5.2.5.0, 5.2.5.1, 5.2.6.0, 5.2.6.1
5.1
5.1.0.0, 5.1.1.0, 5.1.2.0, 5.1.3.0, 5.1.4.0, 5.1.5.0, 5.1.5.1, 5.1.6.0, 5.1.7.0, 5.1.8.0, 5.1.8.1, 5.1.9.0, 5.1.10.0
5.0
5.0.1.0, 5.0.1.1, 5.0.2.0, 5.0.2.1, 5.0.2.2, 5.0.2.3, 5.0.3.0, 5.0.3.1, 5.0.4.0, 5.0.4.1, 5.0.5.0, 5.0.5.1, 5.0.5.2, 5.0.5.3, 5.0.5.4
Troubleshooting
The Common Name (CN) configured in the certificate must match the address used in browser. If the SSL certificate CN=testserver.delphix.com, the browser address used to access the interface must also be https://testserver.delphix.com. Using https://testserver would be expected to fail in this instance.
Resolution
If the requirements mentioned in Troubleshooting section do not explain the behavior, the issue may be related to behavioral changes introduced in Firefox and Chrome. Although the Subject Alternative Name (SAN) is technically optional, modern browsers now include additional checks with SAN against the CN, and both must be populated.
There are multiple methods available to confirm this as the root cause.
1. The uploaded/active HTTPS certificate can be reviewed in System Setup.
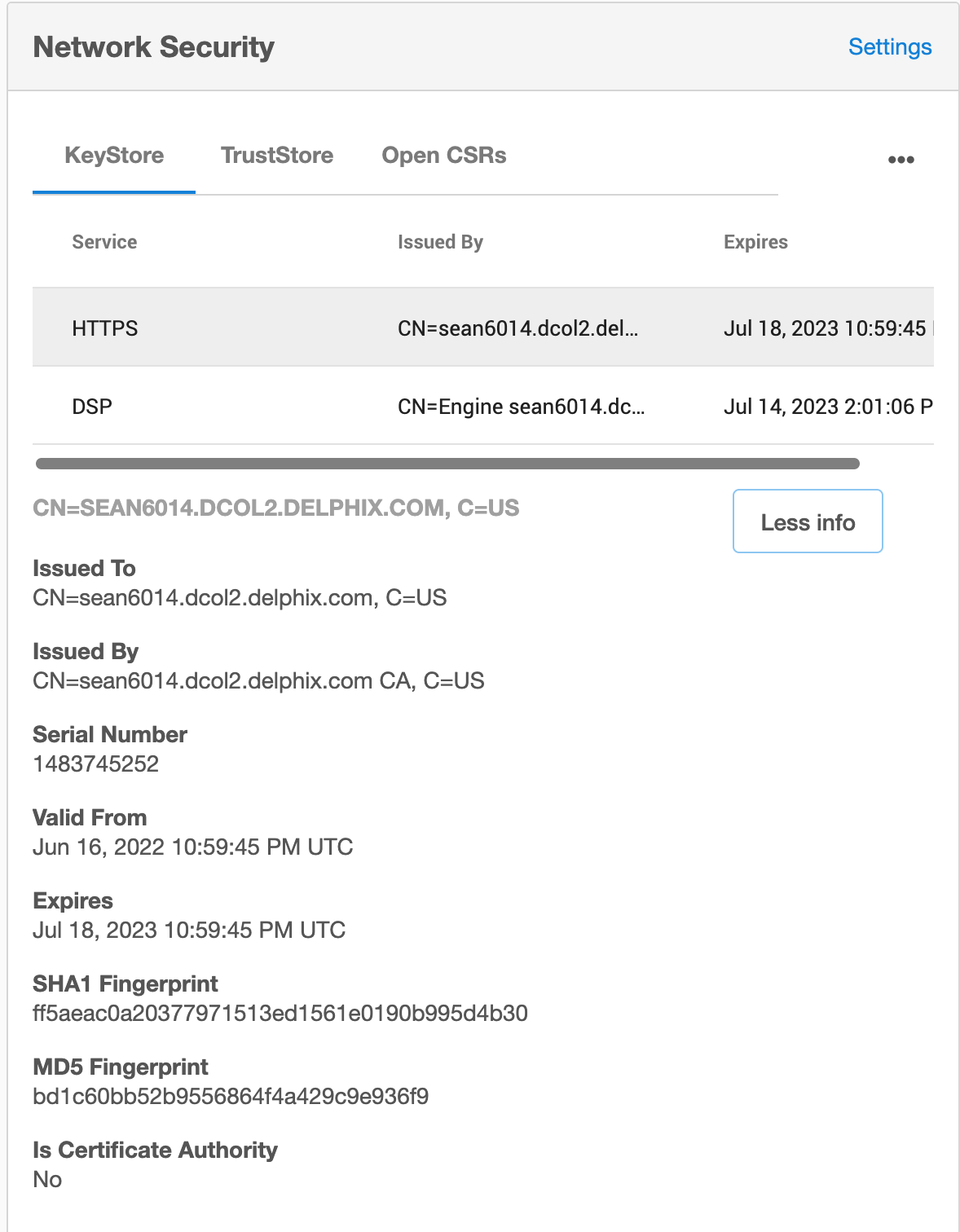
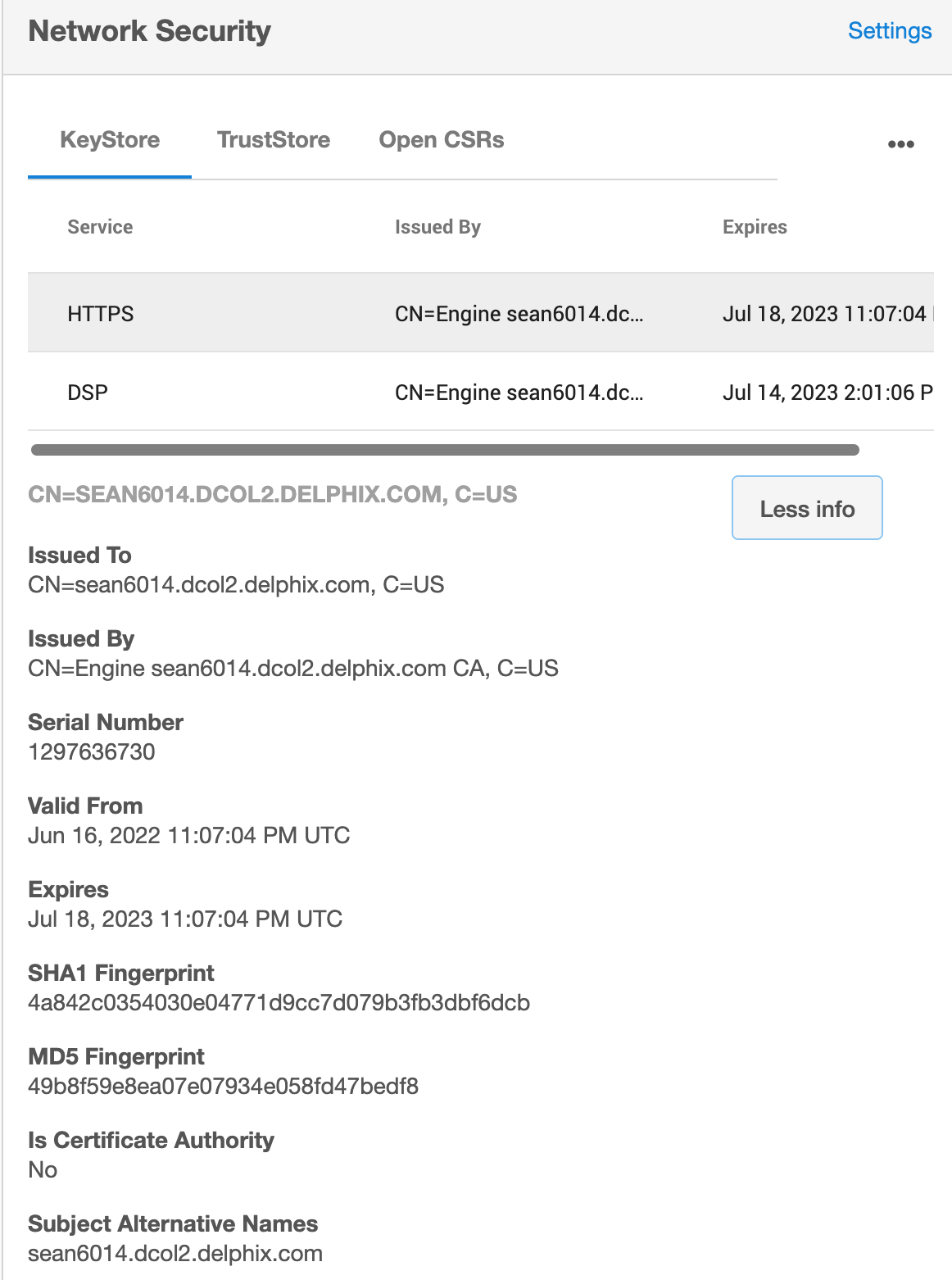
This can be verified by reviewing the certificate details uploaded to the Engine under the KeyStore tab in Network Security, and then and clicking More Info. In the first example, no SAN exists; In the second example, we see Subject Alternative Names exists at the bottom of this panel:
2. The Engine certificate details can be reviewed in a browser
Methods may vary depending on the browser version, but generally a user can click the Not Secure text indicated in address bar to view details about the insecure connection:
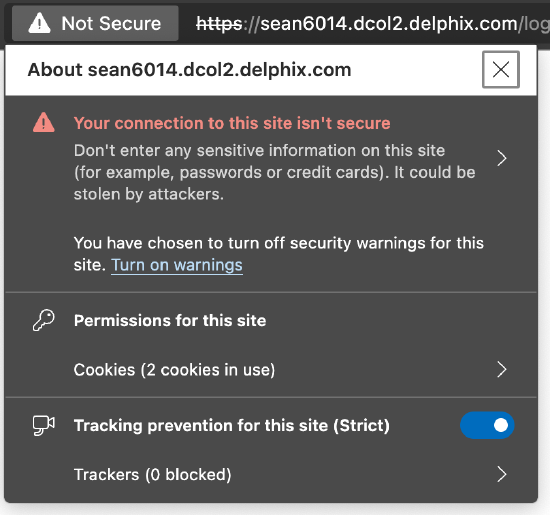
From here, the details of the certificate can be interrogated. From the example above, clicking the Your connection is not secure field will lead to another dialog, with a Certificate icon indicated on the right-hand side:
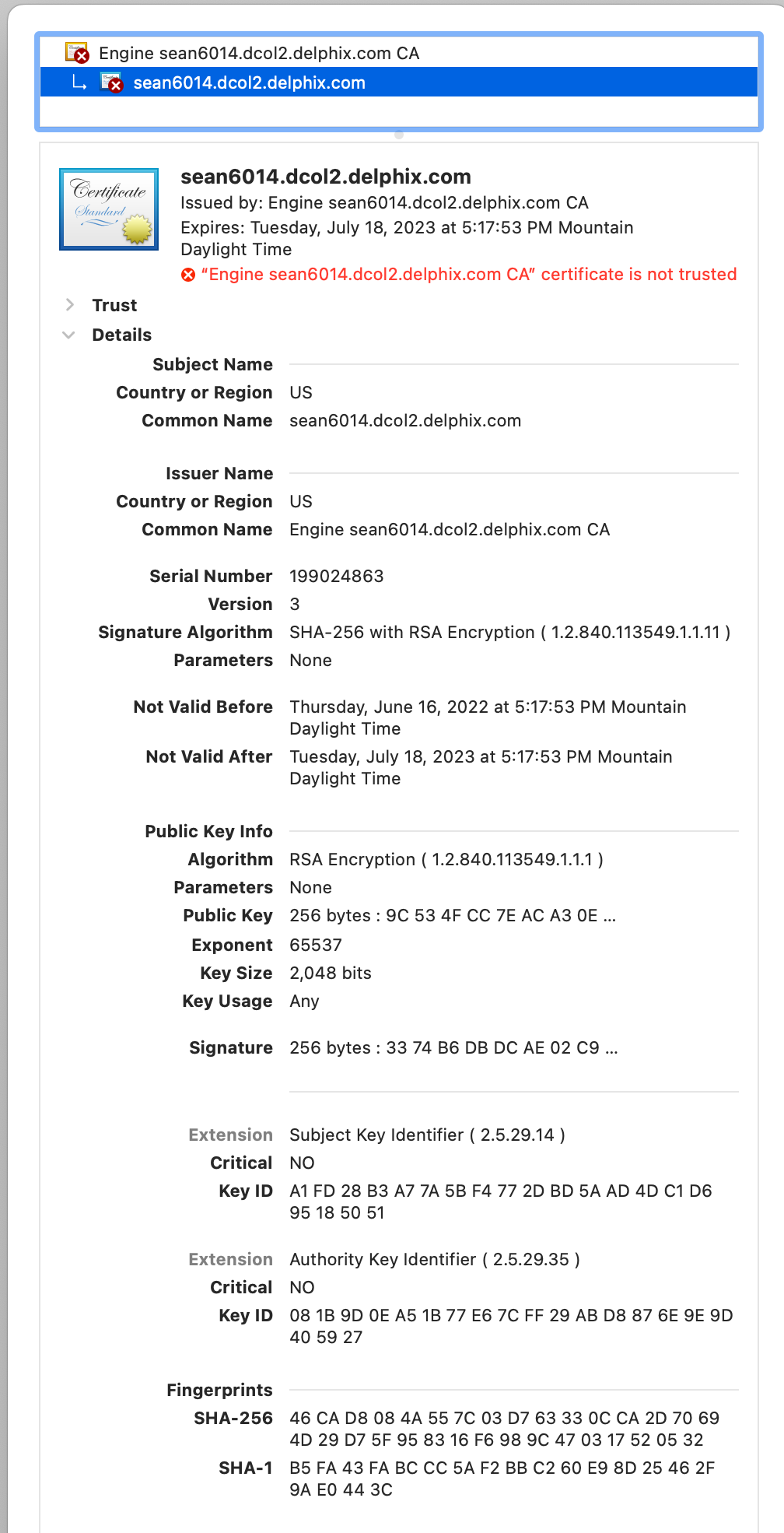
Clicking this message leads to a new Browser pop-up window, where Details can be expanded to view the details of the SSL certificate received. In the example below, we find no Subject Alternative Name configured.
3. The CSR used for certificate signing can be reviewed
If the CSR has been saved, it can be reviewed via openssl. In the first example, Attributes indicates none, and likewise Requested Extensions is blank.
$ openssl req -in ./csrnosan.csr -text -noout
Certificate Request:
Data:
Version: 1 (0x0)
Subject: C = US, ST = Colorado, L = Arvada, O = Delphix, OU = Support, CN = sean6014.dcol2.delphix.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b4:c8:c6:2e:40:74:42:69:da:ea:d8:0b:51:fe:
67:9c:05:4e:40:02:75:da:c0:38:b9:52:dc:b9:6a:
10:04:27:f2:2e:f0:8c:62:69:87:4b:8a:49:91:13:
80:bb:25:9e:89:69:3e:6f:7e:36:32:8e:d2:db:d5:
4e:9c:da:1d:13:44:b5:5d:b2:48:27:9c:2b:a2:d4:
be:cc:a1:88:43:dd:c4:8b:8b:1e:0b:23:bf:c0:d5:
7b:1a:ce:a1:d6:68:bd:c0:de:7b:62:50:ee:6a:48:
3f:1f:43:64:77:3b:9c:4f:55:11:8a:af:09:43:1a:
78:63:2c:6d:88:e8:50:05:f6:d9:e6:17:7c:ae:b0:
fa:62:af:43:03:85:20:36:a1:2f:94:c1:3e:b1:d3:
68:f5:32:73:b6:64:b6:85:12:d2:8c:cb:0a:3c:99:
fd:1a:5a:ac:0e:34:32:67:ea:28:d8:fd:09:ad:12:
d5:02:62:00:f5:2f:67:09:26:52:83:d8:7c:44:23:
fc:9c:57:08:97:d9:4c:59:d9:f9:1a:7a:c5:e5:15:
25:21:34:16:3b:b8:71:fb:c6:fe:79:9d:f5:d8:37:
f3:9d:c8:c2:f5:48:35:9a:18:4b:fe:b1:72:93:73:
8b:31:bf:2f:c8:a9:2a:9d:6f:30:77:76:26:6a:fb:
a6:13
Exponent: 65537 (0x10001)
Attributes:
(none)
Requested Extensions:
...
In the second example, we see X509v3 Subject Alternative Name exists:
$ openssl req -in ./csrsan.csr -text -noout
Certificate Request:
Data:
Version: 1 (0x0)
Subject: C = US, ST = Colorado, L = Arvada, O = Delphix, OU = Support, CN = sean6014.dcol2.delphix.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b8:1c:74:de:89:d5:16:16:86:0a:da:df:d0:a8:
81:38:f2:cf:57:bb:9e:d5:69:81:2c:01:a2:0d:61:
27:47:8d:e7:1b:b3:34:f6:84:13:b9:50:ad:d1:29:
60:1a:02:2d:77:c5:98:c8:7a:19:b2:11:7c:58:f4:
8b:bb:74:a1:60:dc:2d:43:6d:96:fc:83:f2:34:74:
8d:ff:19:40:c9:62:8f:59:49:cb:02:bc:26:9d:76:
16:75:6e:0f:4d:e7:0e:fb:30:32:4f:f5:56:34:29:
fa:3f:d6:67:4a:b6:ac:46:a1:9a:90:13:d8:26:d7:
8b:ec:8b:46:9f:d2:76:9c:af:c0:92:8e:df:6e:7e:
56:16:d8:d0:7b:1c:58:77:26:9c:85:24:1c:28:91:
c0:32:28:18:8a:1c:41:9b:8b:cf:8f:48:c7:94:49:
5c:53:bb:88:82:cb:da:38:8f:61:a8:3b:5c:ed:12:
14:8e:78:db:dd:47:c3:df:db:30:f1:15:0c:2d:8b:
50:1d:4d:29:14:43:45:0c:80:33:36:a1:e7:33:44:
c1:d2:17:48:a6:6e:12:da:20:95:f7:60:17:fc:e5:
fa:ed:8b:a6:86:9b:0f:02:24:9d:cf:f3:ff:26:a9:
81:a4:db:7a:0b:e9:4b:75:65:a5:59:9c:08:d8:01:
38:87
Exponent: 65537 (0x10001)
Attributes:
Requested Extensions:
X509v3 Subject Alternative Name:
DNS:sean6014.dcol2.delphix.com
...
Once the absence of a SAN is confirmed, it is recommended to regenerate the certificate by either generating a new keystore, or a new CSR (depending on the original method used for replacement), with the SAN including the CN hostname (optionally including other parameters such as wildcard domain, hostname or FQDN, et cetera).
This detail is also indicated in our Documentation:
https://cd.delphix.com/docs/latest/delphix-provided-key-pair-configuration
Subject Alternative Names (SAN): Add IP addresses or hostnames to be associated with the certificate. Some browsers require that the HTTPS certificate includes the server's fully qualified domain name (FQDN) as a SAN.
References to this new requirement are provided in the Related Articles section below.
Related Articles
The following articles may provide more information or related information to this article:
