Critical Faults Related to End Entity or Truststore Certificates (KBA10221)
KBA
KBA# 10221
Issue
Critical or warning faults may be registered by the Delphix Engine with titles:
WARNING The certificate for end-entity "HTTPS - Engine" expires on 2023/06/14 17:23:10 EST. CRITICAL The certificate for end-entity "DSP - Engine" has expired. CRITICAL The certificate for end-entity "HTTPS - Engine" has expired. CRITICAL The truststore certificate "CN=<engine name> CA, O=Delphix, C=US", serial number #######, has expired.
These faults indicate the certificates used for the Delphix Session Protocol (DSP) or secure HTTP (HTTPS) are approaching expiration or have expired.
Applicable Delphix Versions
- Click here to view the versions of the Delphix engine to which this article applies
-
Date Release June 21, 2023 12.0.0.0 May 25, 2023 11.0.0.0 Apr 13, 2023 10.0.0.0 | 10.0.0.1 Mar 13, 2023 | Mar 20, 2023 9.0.0.0 | 9.0.0.1 Feb 13, 2023 8.0.0.0 Jan 12, 2023 7.0.0.0 Releases Prior to 2023 Major Release All Sub Releases 6.0 6.0.0.0, 6.0.1.0, 6.0.1.1, 6.0.2.0, 6.0.2.1, 6.0.3.0, 6.0.3.1, 6.0.4.0, 6.0.4.1, 6.0.4.2, 6.0.5.0, 6.0.6.0, 6.0.6.1, 6.0.7.0, 6.0.8.0, 6.0.8.1, 6.0.9.0, 6.0.10.0, 6.0.10.1, 6.0.11.0, 6.0.12.0, 6.0.12.1, 6.0.13.0, 6.0.13.1, 6.0.14.0, 6.0.15.0, 6.0.16.0, 6.0.17.0, 6.0.17.1, 6.0.17.2
5.3
5.3.0.0, 5.3.0.1, 5.3.0.2, 5.3.0.3, 5.3.1.0, 5.3.1.1, 5.3.1.2, 5.3.2.0, 5.3.3.0, 5.3.3.1, 5.3.4.0, 5.3.5.0, 5.3.6.0, 5.3.7.0, 5.3.7.1, 5.3.8.0, 5.3.8.1, 5.3.9.0 5.2
5.2.2.0, 5.2.2.1, 5.2.3.0, 5.2.4.0, 5.2.5.0, 5.2.5.1, 5.2.6.0, 5.2.6.1
5.1
5.1.0.0, 5.1.1.0, 5.1.2.0, 5.1.3.0, 5.1.4.0, 5.1.5.0, 5.1.5.1, 5.1.6.0, 5.1.7.0, 5.1.8.0, 5.1.8.1, 5.1.9.0, 5.1.10.0
5.0
5.0.1.0, 5.0.1.1, 5.0.2.0, 5.0.2.1, 5.0.2.2, 5.0.2.3, 5.0.3.0, 5.0.3.1, 5.0.4.0, 5.0.4.1, 5.0.5.0, 5.0.5.1, 5.0.5.2, 5.0.5.3, 5.0.5.4
Delphix Certificates Explained
The Delphix Engine automatically generates self-signed certificate for DSP and HTTPS use; these certificates will be signed by a self-generated certificate authority (CA). Typically these will be referenced as "self-signed" certificates.
These can be replaced as needed with custom certificates, but in either case, the Engine will monitor for expiration of these certificates, and will generate faults accordingly.
Self-signed certificates may be valid for 4 years from date of Engine installation, or 397 days from date of Engine installation. This will vary depending on the original Engine version installed.
DSP
DSP certificate are only used if Custom Authorizations are configured, which typically also use a signed replacement certificate. Custom Authorizations enable the usage of Engine certificates in Environment communication, Engine Replication, or Network Performance Testing.
Note, these apply to Continuous Data Engines only; Continuous Compliance Engines do not leverage DSP.
HTTPS
HTTPS certificates are only used if the Engine has HTTP disabled, or if HTTPS connectivity is used in the Environment (indicated in browser address bar by https:// prepended to Engine address). These may also be self-signed, or using a signed replaced certificate.
Symptoms
Whether this fault is of concern ultimately depends on the use of the Engine, connectivity, and the security configuration.
- If HTTPS is not in use, the expiration of an installed certificate can be marked Ignored, as it's not relevant to the current Engine access methods. There will be no difference in access.
- If HTTPS is in use, the connection may be indicated as untrusted by the web browser used to access the Engine once certificate expires. However, access will not be blocked.
Resolution
Administrators have several options available depending on the current Engine usage. It is at this time we also strongly recommend that the Delphix Administrator confer with their IT or Security teams to ensure compliance with any internal policies for trusted connections.
- If certificates are actively used, they can be replaced. Whether self-generated (self-signed) certificates are regenerated or new certificates are generated and signed by a trusted authority depends on infrastructure requirements. The details of these processes can be found in Product Documentation:
Regenerating Self-signed end-entity certificates - https://cd.delphix.com/docs/latest/regenerating-self-signed-end-entity-and-ca-certifi
Delphix provided key pair configuration (this option may not be viable if the CA certificate has expired) - https://cd.delphix.com/docs/latest/delphix-provided-key-pair-configuration
Customer provided key pair configuration - https://cd.delphix.com/docs/latest/customer-provided-key-pair-configuration
Replacement processes are fully customer-serviceable, and do not require Support intervention to complete.
- If certificates are not actively used, the faults can be ignored. There will be no functional issue in doing this, and the certificates can still be replaced at a later date if so desired.
CA Certificates
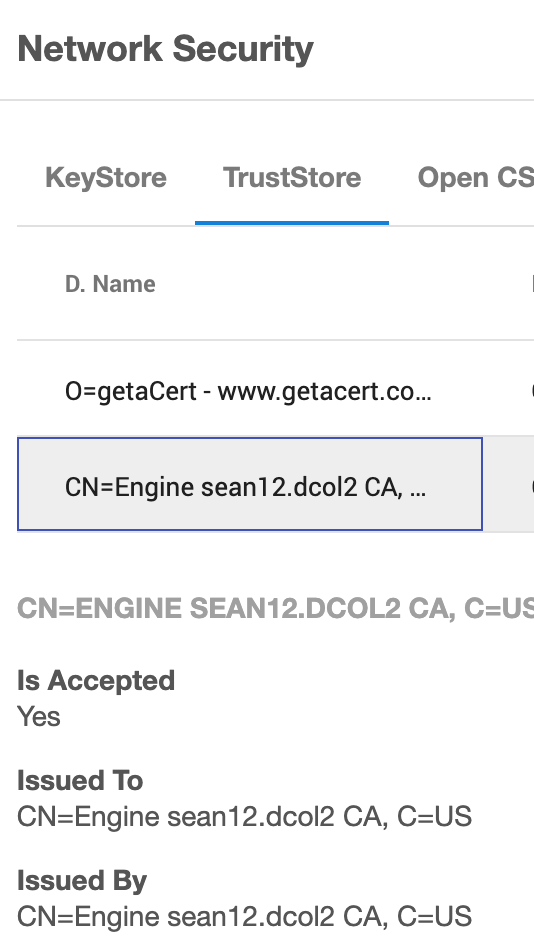
One deviation does exist, in that the initial CA certificate generated by the Engine at installation currently can not be removed. A new CA certificate can be installed as needed to establish chain of trust, but the initial CA certificate is currently blocked from removal. As a result, regardless of the resolution path selected, the fault related to the original self-generated CA certificate will have to be marked Ignored.
A self-generated CA certificate will include "Engine <engine name> CA" in the Issued By and Issued To fields when selected in the truststore.
Related Articles
The following articles may provide more information or related information to this article:
-
Regenerating Self-signed end-entity certificates - https://cd.delphix.com/docs/latest/regenerating-self-signed-end-entity-and-ca-certifi
Delphix provided key pair configuration (this option may not be viable if the CA certificate has expired) - https://cd.delphix.com/docs/latest/delphix-provided-key-pair-configuration
Customer provided key pair configuration - https://cd.delphix.com/docs/latest/customer-provided-key-pair-configuration
