Changing the Delphix OS (Operating System) User's Windows Authentication (Active Directory) Password for SQL Server Environments (KBA5834)
KBA
KBA# 5834
Issue
The Continuous Data Engine interacts with Windows Environments using Active Directory (AD) authentication, typically using user accounts that were created specifically for use with the Continuous Data Engine.
In situations where these Active Directory account passwords are rotated or changed, the corresponding credentials will also need to be updated within the Continuous Data Engine.
If this is not done, scheduled jobs or monitoring performed by the Continuous Data Engine will fail, and Alerts or Faults will be generated.
The following procedure can be used to help plan and perform a password change that involves Active Directory accounts associated with the Continuous Data Engine.
Prerequisites
In order to follow this procedure, you will need to:
- Have access to your Active Directory or System Administrators
- Have Administrative access to the Continuous Data Engine
- Know the usernames for all Active Directory accounts where the password is being changed
- Know the new password for all Active Directory accounts where the password is being changed
Applicable Delphix Versions
- Click here to view the versions of the Delphix engine to which this article applies
-
Date Release Jun 20, 2024 24.0.0.0 May 22, 2024 23.0.0.0 Apr 17, 2024 | May 8, 2024 22.0.0.0 | 22.0.0.1 Mar 20, 2024 | Apr 2, 2024 21.0.0.0 | 21.0.0.1 Feb 21, 2024 20.0.0.0 Jan 25, 2024 19.0.0.0 Dec 20, 2023 | Jan 10, 2024 18.0.0.0 | 18.0.0.1 Nov 21, 2023 17.0.0.0 Oct 18, 2023 16.0.0.0 Sep 21, 2023 15.0.0.0 Aug 24, 2023 14.0.0.0 Jul 24, 2023 13.0.0.0 Jun 21, 2023 12.0.0.0 May 25, 2023 11.0.0.0 Apr 13, 2023 10.0.0.0 | 10.0.0.1 Mar 13, 2023 | Mar 20, 2023 9.0.0.0 | 9.0.0.1 Feb 13, 2023 8.0.0.0 Jan 12, 2023 7.0.0.0 Releases Prior to 2023 Major Release All Sub Releases 6.0 6.0.0.0, 6.0.1.0, 6.0.1.1, 6.0.2.0, 6.0.2.1, 6.0.3.0, 6.0.3.1, 6.0.4.0, 6.0.4.1, 6.0.4.2, 6.0.5.0, 6.0.6.0, 6.0.6.1, 6.0.7.0, 6.0.8.0, 6.0.8.1, 6.0.9.0, 6.0.10.0, 6.0.10.1, 6.0.11.0, 6.0.12.0, 6.0.12.1, 6.0.13.0, 6.0.13.1, 6.0.14.0, 6.0.15.0, 6.0.16.0, 6.0.17.0, 6.0.17.1, 6.0.17.2
5.3
5.3.0.0, 5.3.0.1, 5.3.0.2, 5.3.0.3, 5.3.1.0, 5.3.1.1, 5.3.1.2, 5.3.2.0, 5.3.3.0, 5.3.3.1, 5.3.4.0, 5.3.5.0, 5.3.6.0, 5.3.7.0, 5.3.7.1, 5.3.8.0, 5.3.8.1, 5.3.9.0 5.2
5.2.2.0, 5.2.2.1, 5.2.3.0, 5.2.4.0, 5.2.5.0, 5.2.5.1, 5.2.6.0, 5.2.6.1
5.1
5.1.0.0, 5.1.1.0, 5.1.2.0, 5.1.3.0, 5.1.4.0, 5.1.5.0, 5.1.5.1, 5.1.6.0, 5.1.7.0, 5.1.8.0, 5.1.8.1, 5.1.9.0, 5.1.10.0
5.0
5.0.1.0, 5.0.1.1, 5.0.2.0, 5.0.2.1, 5.0.2.2, 5.0.2.3, 5.0.3.0, 5.0.3.1, 5.0.4.0, 5.0.4.1, 5.0.5.0, 5.0.5.1, 5.0.5.2, 5.0.5.3, 5.0.5.4
Resolution
The following steps can be used to plan and perform a password change for Active Directory accounts used by the Continuous Data Engine. Each of these steps is explained in more detail below.
- Verify account lockout policies
- Identify Environments where the AD account is used
- Identify dSources where the AD account is used
- [Optional] Disable dSources, VDBs, and Environments
- Change the password in Active Directory
- Update the password in Environments where the AD account is used
- Update the password in dSources where the AD account is used, if required
- Resolve any Faults
- [Optional] Enable dSources, VDBs and Environments
- Monitor for faults or errors
Step 1: Verify account lockout policies
Contact your Active Directory administrators to check whether any account lockout policies are in place for the Active Directory accounts being modified.
If an account lockout policy is in place, it should be temporarily disabled while this procedure is being followed.
If the account becomes locked, it will not be possible to validate and change the passwords.
Step 2: Identify Environments where the AD account is used
Login to the Continuous Data Engine Management interface.
From the Manage → Environments screen, select each Environment. Note which of them include affected Active Directory account(s) in the list of Environment Users.
Alternatively, the Command Line Interface can be used to list the Environments and Users connected to your engine:
/environment/user list display=environment,name ENVIRONMENT NAME WINDOWSTARGET WINDOWSTARGET/DOMAIN\username WINDOWSSOURCE WINDOWSSOURCE/DOMAIN\username
Step 3: Identify dSources where the AD account is used
In some cases, dSources may be configured with an Active Directory username and password.
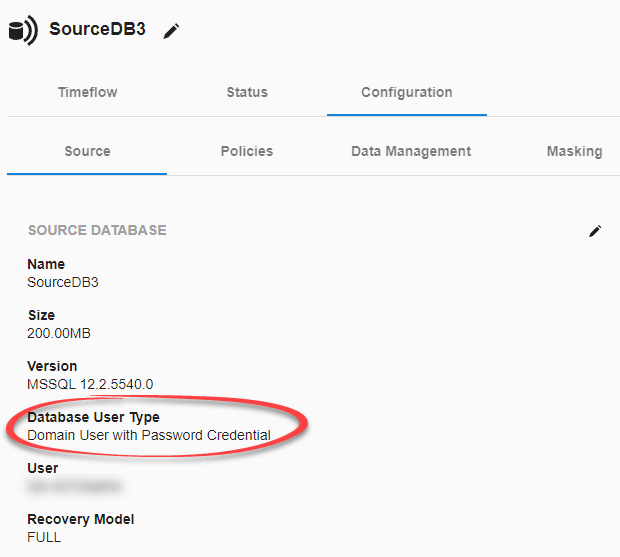
This can be checked using the Manage → Datasets screen. Select each dSource and review the Configuration → Source tab.
If the user type is set to Domain User with Password Credential, make a note of this. This password will also need to be updated in a later step.
From the Command Line Interface, the following command will show the way that the Continuous Data Engine is authenticating to each dSource;
/source list display=name,syncStrategy.mssqlUser.type,syncStrategy.mssqlUser.user NAME SYNCSTRATEGY.MSSQLUSER.TYPE SYNCSTRATEGY.MSSQLUSER.USER SourceDB1 MSSqlDatabaseUser delphix_db SourceDB2 MSSqlEnvironmentUser WINDOWSSOURCE/DOMAIN\username SourceDB3 MSSqlDomainUser DOMAIN\username VDB1 - -
In the CLI output, entries which show a user type of MSSqlDomainUser will need to have their password modified.
Step 4: [Optional] Disable dSources, VDBs and Environments
In some cases, you may wish to disable objects within the Continuous Data Engine prior to password changes.
If account lockout policies cannot be changed, or you are concerned about login failures being reported on Source Databases, use the Management interface, CLI or API to disable dSources.
If account lockout policies cannot be changed, or you are concerned about login failures being reported on Target Environments, use the Management interface, CLI or API to disable VDBs and Environments.
Step 5: Change the password in Active Directory
Once you know where the passwords will need to be updated, you (or your System Administrators) can change the password within Active Directory.
Once this step is complete, the passwords recorded in the engine will no longer be valid. The engine may begin raising faults as it begins to connect to Environments using the outdated credentials.
Step 6: Update the password in Environments where the AD account is used
Login to the Management interface and navigate to the Manage → Environments screen.
For each of the Environments identified during Step 2:
- Select the Environment from the list.
- Click on the username of the affected account, to select it.
- Click the Edit
icon to modify the credential.
- Enter the new password.
- Press Save. The Engine will automatically attempt to verify and store the new password. If the credential is incorrect, or the AD account is locked, this action will fail.
If the user account continues to be locked out, this can cause the GUI update to fail, as the Engine will automatically attempt to test/verify the credential update. To avoid this, the password credential can be updated through CLI, which only updates the stored credential without attempting to verify it. In the example below, the existing AD credential for sl-ad\delphix on Environment win-2022-tgt will be updated.
de-mercury> /environment user
de-mercury environment user> ls
Objects
NAME
Oracle Source 19.11.0.0/oracle
delphix
Oracle Target 19.11.0.0/oracle
win-2022-tgt/sl-ad\delphix
win-2022-src/sl-ad\delphix
Operations
create
de-mercury environment user> select win-2022-tgt/sl-ad\delphix
de-mercury environment user 'win-2022-tgt/sl-ad\delphix'> ls
Properties
type: EnvironmentUser
name: win-2022-tgt/sl-ad\delphix
credential:
type: PasswordCredential
password: ********
environment: win-2022-tgt
groupId: 0
reference: HOST_USER-17
userId: 0
Operations
delete
update
de-mercury environment user 'win-2022-tgt/sl-ad\delphix'> update
de-mercury environment user 'win-2022-tgt/sl-ad\delphix' update *> set credential.password=newpass
de-mercury environment user 'win-2022-tgt/sl-ad\delphix' update *> commit
As the CLI ultimately invokes an API request, any alterative method that issues API POST to /resources/json/delphix/environment/user/ endpoint with appropriate payload can be used to automate the update process (custom CURL script, dxToolkit, etc). The internal user reference will need to be determined.
=== POST /resources/json/delphix/environment/user/HOST_USER-17 ===
{
"type": "EnvironmentUser",
"credential": {
"type": "PasswordCredential",
"password": "newpass"
}
}
Further guidance in API/CLI specifics are beyond the scope of this document.
Step 7: Update the password in dSources where the AD account is used, if required
In many cases, Step 3 will not identify any dSources using Domain User with Password credentials, and this step can be skipped.
If some dSources are using this configuration, for each of the affected dSources:
- Select the dSource in the Manage → Datasets screen.
- Switch to the Configuration → Source tab.
- Press the Edit
icon in the Source Database panel to modify the credential.
- Enter the new password.
- Press Save to validate and store the new password. In contrast to the Environment user update, this action does not automatically validate the user credential, so if the password is incorrect or the AD account is locked, it will not be immediately evident after this change.
Step 8: Resolve any Faults
The engine should now be authenticating to all environments using the correct credentials.
If any authentication failures occurred while Steps 5-7 were being followed, a Fault will be raised in the Continuous Data Engine.
These authentication failures can be marked as Resolved from the System → Faults screen. If they re-occur, a new fault will be posted.
Step 9: [Optional] Enable dSources, VDBs and Environments
If objects were disabled in Step 4, these can be re-enabled now.
Environment Enable operations should be allowed to run through to completion before dSources and VDBs are enabled.
Step 10: Monitor for faults or errors
VDBs and dSources should now be operating normally, with no further errors reported.
Continue to monitor the Continuous Data Engine and your Source and Target Environments for new errors.
