How to Investigate Certificates (Windows) (KBA10541)
KBA
KBA#Applicable Delphix Versions
- Click here to view the versions of the Delphix engine to which this article applies
-
Date Release Oct 18, 2023 16.0.0.0 Sep 21, 2023 15.0.0.0 Aug 24, 2023 14.0.0.0 Jul 24, 2023 13.0.0.0 Jun 21, 2023 12.0.0.0 May 25, 2023 11.0.0.0 Apr 13, 2023 10.0.0.0 | 10.0.0.1 Mar 13, 2023 | Mar 20, 2023 9.0.0.0 | 9.0.0.1 Feb 13, 2023 8.0.0.0 Jan 12, 2023 7.0.0.0 Releases Prior to 2023 Major Release All Sub Releases 6.0 6.0.0.0, 6.0.1.0, 6.0.1.1, 6.0.2.0, 6.0.2.1, 6.0.3.0, 6.0.3.1, 6.0.4.0, 6.0.4.1, 6.0.4.2, 6.0.5.0, 6.0.6.0, 6.0.6.1, 6.0.7.0, 6.0.8.0, 6.0.8.1, 6.0.9.0, 6.0.10.0, 6.0.10.1, 6.0.11.0, 6.0.12.0, 6.0.12.1, 6.0.13.0, 6.0.13.1, 6.0.14.0, 6.0.15.0, 6.0.16.0, 6.0.17.0, 6.0.17.1, 6.0.17.2
5.3
5.3.0.0, 5.3.0.1, 5.3.0.2, 5.3.0.3, 5.3.1.0, 5.3.1.1, 5.3.1.2, 5.3.2.0, 5.3.3.0, 5.3.3.1, 5.3.4.0, 5.3.5.0, 5.3.6.0, 5.3.7.0, 5.3.7.1, 5.3.8.0, 5.3.8.1, 5.3.9.0 5.2
5.2.2.0, 5.2.2.1, 5.2.3.0, 5.2.4.0, 5.2.5.0, 5.2.5.1, 5.2.6.0, 5.2.6.1
5.1
5.1.0.0, 5.1.1.0, 5.1.2.0, 5.1.3.0, 5.1.4.0, 5.1.5.0, 5.1.5.1, 5.1.6.0, 5.1.7.0, 5.1.8.0, 5.1.8.1, 5.1.9.0, 5.1.10.0
5.0
5.0.1.0, 5.0.1.1, 5.0.2.0, 5.0.2.1, 5.0.2.2, 5.0.2.3, 5.0.3.0, 5.0.3.1, 5.0.4.0, 5.0.4.1, 5.0.5.0, 5.0.5.1, 5.0.5.2, 5.0.5.3, 5.0.5.4
Summary
How you investigate a certificate also depends on whether this is for a client application investigating a certificate already installed on a server or a for a server application that is failing to install a certificate. Specifically, we can use investigation tools and their output to:
- Verify the certificate chain is unbroken back to the root CA certificate.
- Verify the common name matches the hostname or FQDN of the server.
- Verify that Subject Alternative Names (SANs) exist and that they exactly match the hostname or FQDN used to access the server from the client.
- Verify that no certificate in the chain is outside of the validity period.
- Verify the key length and ensure it is long enough to meet any security requirements you might have.
- Verify that the end entity certificate has the expected alias defined.
- Extract the certificates to PEM files for import to a truststore.
In the examples here, useful information in the output has been highlighted to help the reader understand commands with a great deal of output.
Investigating an In-Use Certificate
The following procedure can be used to extract useful information about the certificate, such as the validity period and chain. If you have not yet installed the root CA or intermediate CA certificates to your client truststore, options are provided for selective certificate export and import. We have provided parallel examples in Google Chrome and Microsoft Edge. However, the reader should be aware that similar methodology exists for Firefox, Safari, Brave, Opera and generally any modern browser.
- Open a Chromium based web browser, such as Google Chrome or Microsoft Edge.
- Navigate to the URL hosting the HTTPS service with the problem certificate.
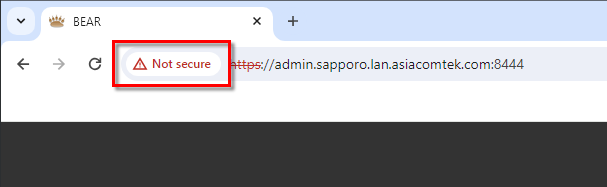
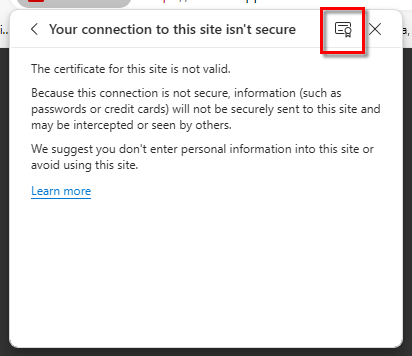
- The address bar will show Not Secure in the address bar. Click it to open the security warning.
| Google Chrome | Microsoft Edge |
 |
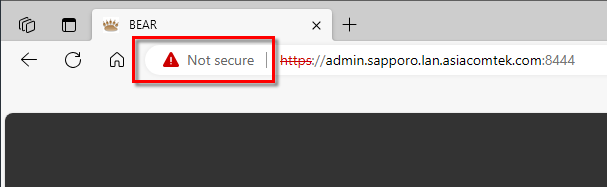 |
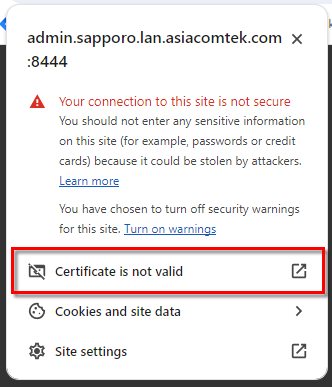
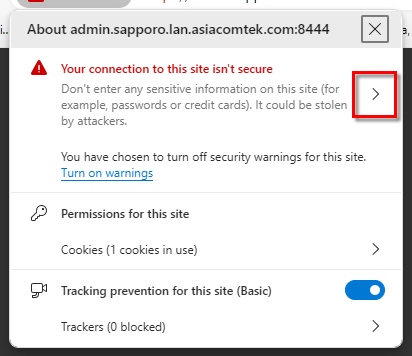
- Click Certificate is not Valid for Chrome or follow the details icon link for Edge. The Certificate Viewer will display.
| Google Chrome | Microsoft Edge |
 |
 |
 |
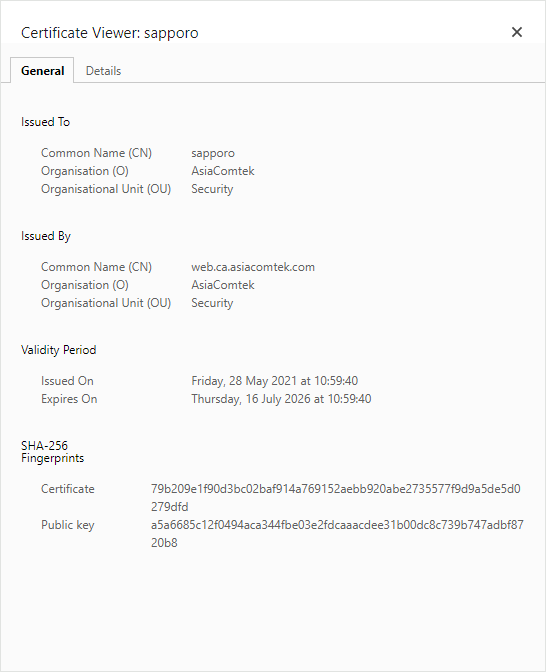
The General tab is active by default and gives you a summary of the end entity certificate. However, the output is abbreviated and even the Distinguished Name is reduced to a few fields. The only trustworthy information on this tab is the Validity Period.
- Select the Details tab. This will provide the information you want.
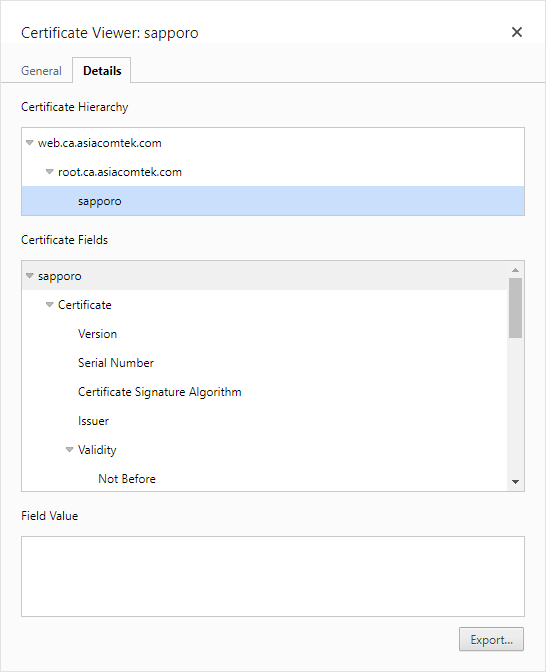
At the top of this tab, the Certificate Hierarchy is another name for Certificate Chain and shows us the chain with the root at the top going down to the end entity certificate at the bottom. You can select any of these to get access to the list of attributes. By navigating this, you see the following:
- The end entity (Server Certificate)
C = JA, ST = Hokkaido, O = AsiaComtek, OU = Security, L = Sapporo, CN = sapporo - ... was signed by intermediate CA certificate
C = JA, ST = Hokkaido, O = AsiaComtek, OU = Security, L = Sapporo, CN = web.ca.asiacomtek.com, emailAddress = developer@asiacomtek.com
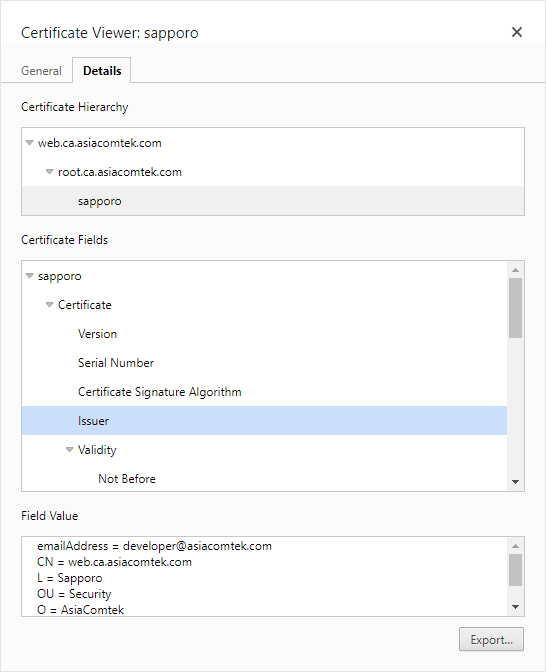
- ... which was in turn signed by root CA certificate C = JA, ST = Hokkaido, L = Sapporo, O = AsiaComtek, OU = Security, CN = root.ca.asiacomtek.com, emailAddress = developer@asiacomtek.com . The chain is unboken because every certificate's Issuer also exists in the output.
- The validity for the end entity certificate is Not Before: May 28 10:59:40 2021 GMT; Not After: Jul 16 01:59:40 2026 GMT which happens to also be the validity period for the chain as well, because it is the latest Not Before value and the earliest Not After value. In some cases, a CA certificate might expire first in which case the validity of the chain would take the earliest Not After timestamp. It is something to be careful of when getting a new certificate from a CA that is near the end of end of its own validity period.
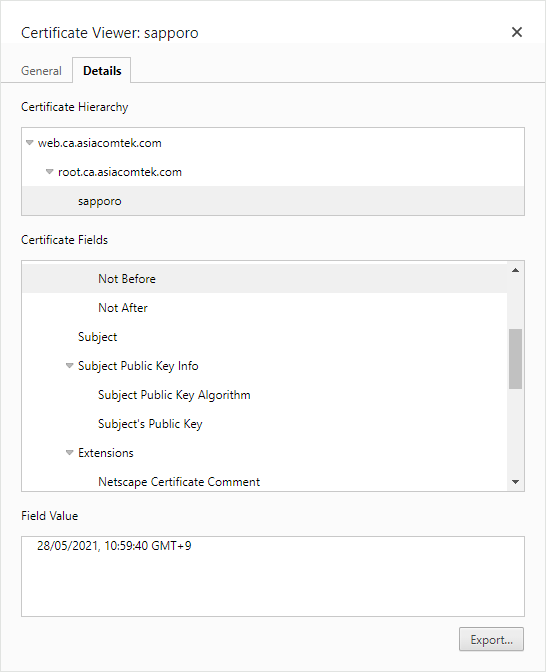
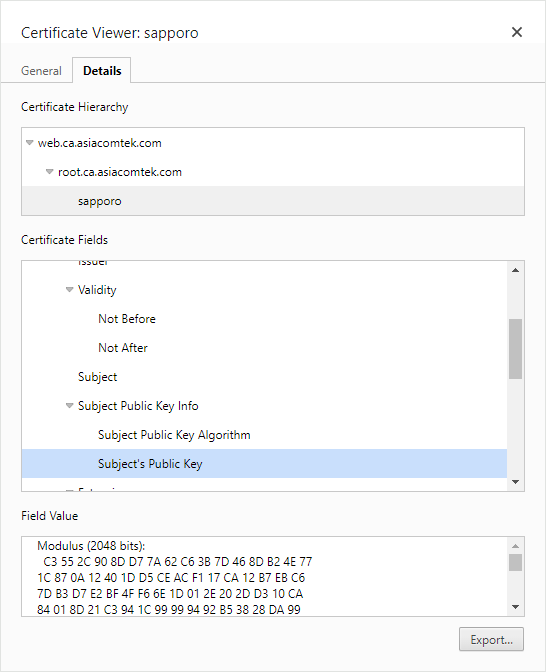
- You can also see that the end entity certificate (Server public key) is 2048 bit. This is useful to know, as applications may impose a minimum length. 2048 bit is the common minimum accepted key length currently, but there are older CAs still issuing 1024 and even 512 bit keys which will be rejected by many applications.
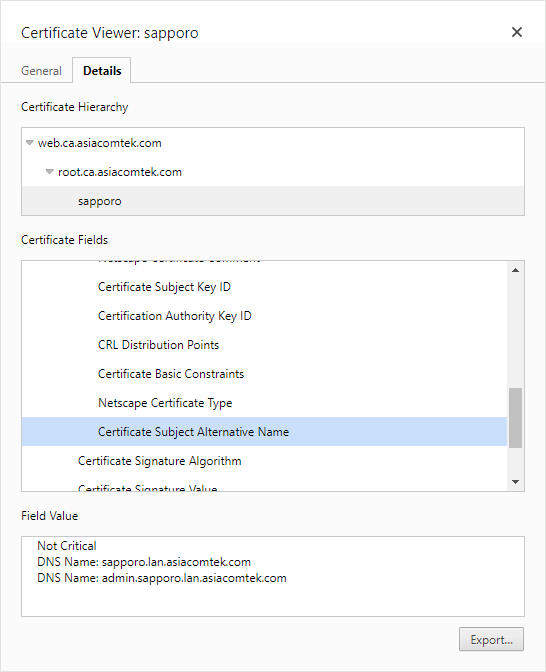
- The Subject Alternative Names (SANs) are also visible here, allowing you to determine whether any of those match the hostname or FQDN used in the URL (valid) or whether the hostname or FQDN used matches none of the SAN entries (invalid).
- Finally, if needed, you can export a certificate, which is useful if you want to export a CA certificate and then import it into the Windows Truststore as a way of resolving problems where the browser reports that the site, page, or certificate is "not trusted".
Investigating a Certificate File
Windows provides several tools for investigating certificates on the command line. For simplicity, certutil can be used to perform purely investigative tasks on both PEM, PKCS#12, and PFX files. The methods described below all provide similar output which allows you to investigate all characteristics of a certificate or all certificates in a keystore file. One command can be used for multiple file types.
> certutil -dump <FILENAME>
PEM
> certutil -dump cert.pem
X509 Certificate:
Version: 3
Serial Number: 989681
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
E=developer@asiacomtek.com
CN=web.ca.asiacomtek.com
L=Sapporo
OU=Security
O=AsiaComtek
S=Hokkaido
C=JA
Name Hash(sha1): 0ae61207c4cc18e1f3dcd62958f04b0438c1bb96
Name Hash(md5): 7596711c9c112fa8260fed41c79e739a
NotBefore: 2021/05/28 10:59
NotAfter: 2026/07/16 10:59
Subject:
CN=sapporo
L=Sapporo
OU=Security
O=AsiaComtek
S=Hokkaido
C=JA
Name Hash(sha1): 7cc5543dcb0e29fe242ca5047d364e2b86f3c4b6
Name Hash(md5): 37db1f678a2339f570287fa248638328
Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA (RSA_SIGN)
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 c3 55 2c 90 8d d7 7a
0010 62 c6 3b 7d 46 8d b2 4e 77 1c 87 0a 12 40 1d d5
0020 ce ac f1 17 ca 12 b7 eb c6 7d b3 d7 e2 bf 4f f6
0030 6e 1d 01 2e 20 2d d3 10 ca 84 01 8d 21 c3 94 1c
0040 99 99 94 92 b5 38 28 da 99 3d 16 12 33 28 87 53
0050 8d cc 72 bb d5 c7 18 6a 92 46 2d b0 67 ad af 99
0060 fe f2 93 22 3f ed a6 1e 5a b4 28 96 ad bb d6 a5
0070 26 80 64 ef 4f e2 25 6b 16 e7 5b 20 87 2b ff ff
0080 88 e9 31 c0 d3 58 99 0a 71 5d 51 fc df 4c 63 a9
0090 92 eb 50 3e 89 3f 02 7b 84 7c 9b 2c 14 97 02 88
00a0 e5 3b 05 5f cb 53 1a 24 d8 ef 60 6e b3 e2 35 9f
00b0 eb a2 ff 2c 8f a6 70 d6 e6 31 41 6c b4 08 8f 23
00c0 4e 86 c6 c5 e4 23 af 5c bd d8 81 b9 b7 8d ff 63
00d0 c2 b3 ba 07 d3 22 b2 0d 88 df 98 55 9e 0c 2e ea
00e0 78 50 24 8b 39 1a ff 84 50 b1 c6 2d fe df c8 82
00f0 df 29 03 97 48 ee 83 5c 14 8a 05 f6 fe 8a 92 44
0100 1e 9d 23 a9 aa c3 b4 5c 8f 02 03 01 00 01
Certificate Extensions: 7
2.16.840.1.113730.1.13: Flags = 0, Length = 29
Netscape Comment
AC X509 Authority Generated Certificate
2.5.29.14: Flags = 0, Length = 16
Subject Key Identifier
8a5b294c6f7e29b3c5ed150186c2b89b89b76029
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=1dc996857ec8c8395029b1a19472aa8b11127972
2.5.29.31: Flags = 0, Length = 83
CRL Distribution Points
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://ca.asiacomtek.com/web.ca.asiacomtek.com.crl
[2]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://ca.asiacomtek.com/b-x509/crls/web.ca.asiacomtek.com.crl
2.5.29.19: Flags = 0, Length = 2
Basic Constraints
Subject Type=End Entity
Path Length Constraint=None
2.16.840.1.113730.1.1: Flags = 0, Length = 4
Netscape Cert Type
SSL Server Authentication (40)
2.5.29.17: Flags = 0, Length = 40
Subject Alternative Name
DNS Name=sapporo.lan.asiacomtek.com
DNS Name=admin.sapporo.lan.asiacomtek.com
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 4d 04 41 c2 eb ec b0 11 2b 2e af 68 88 40 b3 fb
0010 b8 65 76 e3 b8 db 9c 2b 45 32 40 c7 36 ad 5f 0d
0020 9a 32 c1 c8 da ae c4 5d c2 0a f1 3a 6e 1e d8 6e
0030 35 5b d0 a7 b8 34 fe a3 9c e7 8d f7 81 41 6f 3c
0040 d7 68 27 3b 94 94 bd 69 2f 2c a7 12 d6 79 b0 b4
0050 1e ad 0f 83 db bd 42 fb 75 97 a7 dd 05 6d 13 e7
0060 ef a7 46 46 a2 74 4c 49 64 5f 56 21 c4 95 f7 0e
0070 55 cf e6 78 39 de 95 b1 19 db 84 bc 20 0e 20 60
0080 17 59 58 79 f1 8b cf 99 de b5 e6 9f d2 c2 6b af
0090 fa b1 40 f7 a7 e7 37 b7 a6 44 ab 62 bc 98 c1 ea
00a0 5d 1e 59 e4 74 ad b6 03 79 f2 06 02 62 9c 9a ff
00b0 d4 66 ef 99 59 fc c0 ff db dd 7d ee a1 4e 2a 4f
00c0 28 1c d9 d3 45 4b e1 24 a1 41 02 9b 2b 6f 07 cf
00d0 4d c8 e7 4e fa 4f 80 9c 91 4b a3 71 9a 62 75 af
00e0 90 5b 1d 65 c6 b5 81 68 45 38 3a 0f b4 b7 9d d7
00f0 f3 31 0d b0 fd 0e 9c 72 47 f0 34 97 ee ce 78 8a
Non-root Certificate
Key Id Hash(rfc-sha1): 8a5b294c6f7e29b3c5ed150186c2b89b89b76029
Key Id Hash(sha1): 89fc2ac586acdaf3f9062a49b205cb2394290bdb
Key Id Hash(bcrypt-sha1): 913578726f7eaaa80e1db68e29103c7cbdae414d
Key Id Hash(bcrypt-sha256): 058b330fd758be7e7e122a2d159dba4911e48319caad7d0ba3caa0b24a6be777
Key Id Hash(md5): c093c8e5be30a6d2450ce04550567a7a
Key Id Hash(sha256): 11f682a855b9d9e6e621b28189d29a37520c98addc553911ce2bf5146c968336
Key Id Hash(pin-sha256): paZoXBLwSUrKNE++A+L9yqrN7jGwDcjHObdHrb+HILg=
Key Id Hash(pin-sha256-hex): a5a6685c12f0494aca344fbe03e2fdcaaacdee31b00dc8c739b747adbf8720b8
Cert Hash(md5): e024e2c91fc38017e328da41e420e440
Cert Hash(sha1): 9e9a4eee0596b1adfe9fa6f2cdc50e7b212260d5
Cert Hash(sha256): 79b209e1f90d3bc02baf914a769152aebb920abe2735577f9d9a5de5d0279dfd
Signature Hash: 917eb440fe12f92b94646165fd52964566547c883446353cf5f091d91bcdcd90
CertUtil: -dump command completed successfully.
PKCS#12 and PFX
> certutil -v -dump sapporo.p12
Enter PFX password:
================ Certificate 0 ================
================ Begin Nesting Level 1 ================
Element 0:
X509 Certificate:
Version: 3
Serial Number: 989680
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
E=developer@asiacomtek.com
CN=root.ca.asiacomtek.com
OU=Security
O=AsiaComtek
L=Sapporo
S=Hokkaido
C=JA
Name Hash(sha1): 9e964fdacb4fefbb20cac59285c3797bc95317af
Name Hash(md5): 35119da5608e5559af2e50146834643a
NotBefore: 2021/05/27 16:31
NotAfter: 2031/05/25 16:31
Subject:
E=developer@asiacomtek.com
CN=web.ca.asiacomtek.com
L=Sapporo
OU=Security
O=AsiaComtek
S=Hokkaido
C=JA
Name Hash(sha1): 0ae61207c4cc18e1f3dcd62958f04b0438c1bb96
Name Hash(md5): 7596711c9c112fa8260fed41c79e739a
Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA (RSA_SIGN)
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 b1 7f ff 79 ec 6a 22
0010 0d 16 0b 10 73 91 09 39 02 b0 87 83 2a c0 a9 db
0020 17 5f ca 17 6d a1 06 4e 33 d3 1b 2a 8f fc 9b 8d
0030 4c 31 f8 27 eb ca f3 33 f4 dd 29 89 f5 c8 9c 66
0040 db f5 a1 37 12 a8 6d 2c 74 02 bf 33 62 e1 e0 5e
0050 15 69 74 19 3f 8c 74 34 2c a7 cf 61 76 89 e2 2a
0060 07 60 c9 c8 75 76 d3 5c a6 bb e6 86 1c 23 dd 7d
0070 67 71 62 09 1b 14 5b a9 98 b2 79 e3 12 d5 b1 30
0080 02 ac 3e 5e 07 cb 1d f0 8a 36 a8 db e7 b3 3f ed
0090 88 5a 17 6f 24 3c 01 86 e4 31 42 a9 6b 72 5d 83
00a0 82 a0 fc cf 71 d3 97 c1 4c cb 40 81 d8 3c 4c fd
00b0 78 13 a1 88 77 87 a8 60 1c 7b b7 08 bf 78 48 1b
00c0 de 22 d3 86 06 a6 6f af c5 fd 1e b0 f4 7c 80 cd
00d0 09 d5 a9 ec be 7f bd 7d 74 72 a8 63 4d 1b f2 08
00e0 17 9f 2c f5 fb cb 17 fa 8b a1 bd bf 75 9d db 16
00f0 a6 6b 3b c5 4d 99 e7 b4 16 bd f9 ce f0 70 61 a5
0100 f1 46 6f 81 41 fe 74 9c ed 02 03 01 00 01
Certificate Extensions: 7
2.16.840.1.113730.1.13: Flags = 0, Length = 29
Netscape Comment
AC X509 Authority Generated Certificate
2.5.29.14: Flags = 0, Length = 16
Subject Key Identifier
1dc996857ec8c8395029b1a19472aa8b11127972
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=66baf8370d649c61a2ce5efb171f135b1f067946
2.5.29.31: Flags = 0, Length = 85
CRL Distribution Points
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://ca.asiacomtek.com/root.ca.asiacomtek.com.crl
[2]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://ca.asiacomtek.com/b-x509/crls/root.ca.asiacomtek.com.crl
2.5.29.19: Flags = 0, Length = 5
Basic Constraints
Subject Type=CA
Path Length Constraint=None
2.16.840.1.113730.1.1: Flags = 0, Length = 4
Netscape Cert Type
SSL Server Authentication, Signature (50)
2.5.29.17: Flags = 0, Length = 19
Subject Alternative Name
DNS Name=web.ca.asiacomtek.com
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 69 9d e7 84 6e 99 09 17 36 b0 b0 ff ef 60 6c 1c
0010 b4 f7 ce 96 49 26 89 c9 47 10 ce ac e5 91 7a be
0020 63 f3 02 f2 28 06 88 59 4b 0d 31 3b d4 98 4b a6
0030 92 31 66 9a 92 34 8e 98 a8 20 0e be 4d 30 20 b8
0040 d6 45 9f 33 a9 ca f3 9c ab de e0 66 04 df c0 e0
0050 a4 97 53 eb cf 5e 6c f2 c7 63 24 7e 3c 53 9a 5f
0060 5a d1 b0 55 2c 1a 7f 49 70 27 19 97 2a f3 43 62
0070 92 0f ff 7e 10 b2 79 8f 17 91 82 53 96 d5 55 00
0080 57 5a d1 a0 09 12 44 d6 3d 70 52 71 9f ff 11 52
0090 7e f0 1f 56 87 75 e4 d0 82 e0 b0 8a 86 52 65 5d
00a0 dd ff 9e 18 ac 3f 12 d3 a4 e7 d0 ad 7a d8 1b ef
00b0 f6 2e 7e ad 56 2c 7a 66 b5 c1 88 e5 a6 20 18 8c
00c0 29 9e c9 87 d6 89 45 80 36 84 89 25 2c 7e 98 11
00d0 01 25 de c4 05 0b c9 44 a6 87 93 cd 3e 1d 8f 9c
00e0 1f 60 6f 5e 85 0b e7 f7 fc af fd 01 38 db 4d c0
00f0 3d e3 0a d8 02 04 87 3f 1e 7d 29 91 64 c6 c7 a6
Non-root Certificate
Key Id Hash(rfc-sha1): 1dc996857ec8c8395029b1a19472aa8b11127972
Key Id Hash(sha1): 107b2fd91d5db7c256abccd16c868d1d0a7e8788
Key Id Hash(bcrypt-sha1): 00eb837d2c813f788bf9f073a852bf59d8fc1935
Key Id Hash(bcrypt-sha256): ff8e8292af2bcf2041a61b58cab1d2baff753e97c116084a424fb96250d24b23
Key Id Hash(md5): dcc623b2fd5c945128fbc660c111a81b
Key Id Hash(sha256): 9f8c4064ad00e5b43c945f2facb57dc72bb5213792398fd9358e0702b4034202
Key Id Hash(pin-sha256): 4EcFxVyjgbavVvfhND2wMec2ONuJ3VePg87/esrBw2s=
Key Id Hash(pin-sha256-hex): e04705c55ca381b6af56f7e1343db031e73638db89dd578f83ceff7acac1c36b
Cert Hash(md5): f4f605b532a887d9cdac4f0af9477cdb
Cert Hash(sha1): 228b78c61d921f2acb4ec23e6d475a2cb74d90e6
Cert Hash(sha256): 3f161e90f117c41f4a75c6926ba19ce158d1720e7e4737011a9ee5e08a7ea5a4
Signature Hash: 4ba1678747acf1058c23362056e552bb64fa71df2affdc43894df365a8a3f6e5
---------------- End Nesting Level 1 ----------------
CERT_KEY_IDENTIFIER_PROP_ID(20):
1dc996857ec8c8395029b1a19472aa8b11127972
CERT_MD5_HASH_PROP_ID(4):
f4f605b532a887d9cdac4f0af9477cdb
CERT_SHA1_HASH_PROP_ID(3):
228b78c61d921f2acb4ec23e6d475a2cb74d90e6
CERT_FRIENDLY_NAME_PROP_ID(11):
intermediate1
CERT_ACCESS_STATE_PROP_ID(14):
AccessState = 0
Cannot find the certificate and private key for decryption.
================ Certificate 1 ================
================ Begin Nesting Level 1 ================
Element 1:
X509 Certificate:
Version: 3
Serial Number: 15cc639928e61353272811a02361b88fd62affc7
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
E=developer@asiacomtek.com
CN=root.ca.asiacomtek.com
OU=Security
O=AsiaComtek
L=Sapporo
S=Hokkaido
C=JA
Name Hash(sha1): 9e964fdacb4fefbb20cac59285c3797bc95317af
Name Hash(md5): 35119da5608e5559af2e50146834643a
NotBefore: 2021/05/27 16:27
NotAfter: 2036/05/23 16:27
Subject:
E=developer@asiacomtek.com
CN=root.ca.asiacomtek.com
OU=Security
O=AsiaComtek
L=Sapporo
S=Hokkaido
C=JA
Name Hash(sha1): 9e964fdacb4fefbb20cac59285c3797bc95317af
Name Hash(md5): 35119da5608e5559af2e50146834643a
Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA (RSA_SIGN)
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 c1 6f 5f 37 27 bc 1e
0010 fe 9d b9 0d b9 65 72 30 96 bc b8 9a ba fd 78 fb
0020 3a ab 5d e8 6f be f1 ec 1b 1d 5b 56 f5 b9 29 05
0030 ba 65 95 38 06 80 aa 16 96 a0 8f 98 79 89 98 d6
0040 07 1d be cc f8 d4 d3 dd c1 e3 d5 26 15 5e 56 25
0050 4f 7d d6 06 e7 60 ad 44 61 c0 a1 0b 3b aa e4 4d
0060 f0 22 d5 c8 49 02 b3 40 ae 94 83 78 3c 71 0e c6
0070 95 66 30 5a eb 99 f1 0e 4b 6e 41 24 c6 4e 4f d7
0080 8e 28 71 0a 19 fb 92 a2 2e 43 84 c1 be c3 eb 65
0090 b9 0c ba ae 7d 0b 45 ee bd d7 35 a9 64 ac b0 ed
00a0 92 e7 61 a2 d4 bf 19 6d 84 76 76 e5 4b 0f fa 5a
00b0 35 68 01 56 72 12 ef 1c 23 9d ae df 50 65 07 58
00c0 22 64 e6 36 f8 7a a0 be 7e 78 3c 63 70 f3 46 06
00d0 81 4a 3a d9 9b 26 c3 e4 73 9a b3 22 bb d3 15 7f
00e0 dc f4 7a 58 54 ba 8a 57 56 b7 f5 5b 3c 34 07 21
00f0 74 b4 3a 13 34 5c 6a 94 65 d2 5f 7d 0a 74 ff 47
0100 2f b1 89 84 cd 13 5a cc a3 02 03 01 00 01
Certificate Extensions: 5
2.16.840.1.113730.1.13: Flags = 0, Length = 29
Netscape Comment
AC X509 Authority Generated Certificate
2.5.29.14: Flags = 0, Length = 16
Subject Key Identifier
66baf8370d649c61a2ce5efb171f135b1f067946
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=66baf8370d649c61a2ce5efb171f135b1f067946
2.5.29.19: Flags = 0, Length = 5
Basic Constraints
Subject Type=CA
Path Length Constraint=None
2.5.29.31: Flags = 0, Length = 85
CRL Distribution Points
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://ca.asiacomtek.com/root.ca.asiacomtek.com.crl
[2]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://ca.asiacomtek.com/b-x509/crls/root.ca.asiacomtek.com.crl
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 cb 12 47 37 f2 a7 cc 2b 81 92 63 24 2d ee 32 f3
0010 ca e3 5b e8 63 d6 27 db b5 13 95 6c 63 27 f7 e2
0020 4b 02 77 48 2e 7b fb f5 ac 27 eb a8 4d 23 dd 47
0030 42 3b 23 a2 80 82 4b ab 2c 43 e8 74 ed d7 be 6a
0040 6e a0 9f 41 01 af 60 76 24 8e 7c c7 6c d1 bd 56
0050 07 ac 4a f5 de 4f 83 75 a1 9d f3 19 c9 23 9d 6b
0060 67 6a 97 b3 8b ee 46 3b 27 1c 3c f8 07 4b 7b 91
0070 dd cf c6 63 27 c4 9a 14 c2 99 25 b6 07 5c e6 d6
0080 14 1d 99 06 01 e5 c8 81 ca d9 ae 28 79 b4 05 6f
0090 a9 e2 c9 48 8d ab 29 fe 38 22 81 59 d3 e5 86 4c
00a0 86 e9 6f 94 57 30 46 8d 92 60 56 16 af a6 51 c9
00b0 64 40 0f ff 38 24 bf 6e bd a8 d1 0e fc f3 84 38
00c0 20 59 d0 a9 e9 dd cf 88 31 e0 61 2e ea a4 95 71
00d0 22 b1 6b d7 28 c4 7e 12 ea 8d cc 14 0d 27 41 01
00e0 8f 0a c6 5e 9c c8 62 d2 01 1c ad fa 31 6d 1f 2e
00f0 25 f7 81 4a 3c 09 5c 34 7a 9a dc 06 15 2f f5 32
Signature matches Public Key
Root Certificate: Subject matches Issuer
Key Id Hash(rfc-sha1): 66baf8370d649c61a2ce5efb171f135b1f067946
Key Id Hash(sha1): e13aadb587c9f33c9275f833ab7aed18516166de
Key Id Hash(bcrypt-sha1): 3b0c96a1a24aef7e74a31ec772250ebed9cb3437
Key Id Hash(bcrypt-sha256): 952e30daf55ca9078a755e8b1c04ac3aa177a4fdbd08606a32390979ce05b972
Key Id Hash(md5): fdd08e140af4a881328e51b2117dd595
Key Id Hash(sha256): 30ee24581d986aaf4cc762231bdb7cce9990976f7db47824db9f696bf0056d8d
Key Id Hash(pin-sha256): 0ulpUNYzf9JxS4xa5wUx+zrBlXF9wr5SgWT0AUgwzt8=
Key Id Hash(pin-sha256-hex): d2e96950d6337fd2714b8c5ae70531fb3ac195717dc2be528164f4014830cedf
Cert Hash(md5): 3ba32d11a6bd32a6acefd4adaca11730
Cert Hash(sha1): 0d1e48deb01b07ea84c68e9263a6a44b6875f545
Cert Hash(sha256): 92c8eb2bde0e4c0bb1f1de07824678ca6a614948439437bf08ac1a16322669d5
Signature Hash: 2558c420bb85e23744a57e04b19490c9abfa72221f8d1c824cd2af602207b397
---------------- End Nesting Level 1 ----------------
CERT_KEY_IDENTIFIER_PROP_ID(20):
66baf8370d649c61a2ce5efb171f135b1f067946
CERT_MD5_HASH_PROP_ID(4):
3ba32d11a6bd32a6acefd4adaca11730
CERT_SHA1_HASH_PROP_ID(3):
0d1e48deb01b07ea84c68e9263a6a44b6875f545
CERT_FRIENDLY_NAME_PROP_ID(11):
root
CERT_ACCESS_STATE_PROP_ID(14):
AccessState = 0
Cannot find the certificate and private key for decryption.
================ Certificate 2 ================
================ Begin Nesting Level 1 ================
Element 2:
X509 Certificate:
Version: 3
Serial Number: 989681
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
E=developer@asiacomtek.com
CN=web.ca.asiacomtek.com
L=Sapporo
OU=Security
O=AsiaComtek
S=Hokkaido
C=JA
Name Hash(sha1): 0ae61207c4cc18e1f3dcd62958f04b0438c1bb96
Name Hash(md5): 7596711c9c112fa8260fed41c79e739a
NotBefore: 2021/05/28 10:59
NotAfter: 2026/07/16 10:59
Subject:
CN=sapporo
L=Sapporo
OU=Security
O=AsiaComtek
S=Hokkaido
C=JA
Name Hash(sha1): 7cc5543dcb0e29fe242ca5047d364e2b86f3c4b6
Name Hash(md5): 37db1f678a2339f570287fa248638328
Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA (RSA_SIGN)
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 c3 55 2c 90 8d d7 7a
0010 62 c6 3b 7d 46 8d b2 4e 77 1c 87 0a 12 40 1d d5
0020 ce ac f1 17 ca 12 b7 eb c6 7d b3 d7 e2 bf 4f f6
0030 6e 1d 01 2e 20 2d d3 10 ca 84 01 8d 21 c3 94 1c
0040 99 99 94 92 b5 38 28 da 99 3d 16 12 33 28 87 53
0050 8d cc 72 bb d5 c7 18 6a 92 46 2d b0 67 ad af 99
0060 fe f2 93 22 3f ed a6 1e 5a b4 28 96 ad bb d6 a5
0070 26 80 64 ef 4f e2 25 6b 16 e7 5b 20 87 2b ff ff
0080 88 e9 31 c0 d3 58 99 0a 71 5d 51 fc df 4c 63 a9
0090 92 eb 50 3e 89 3f 02 7b 84 7c 9b 2c 14 97 02 88
00a0 e5 3b 05 5f cb 53 1a 24 d8 ef 60 6e b3 e2 35 9f
00b0 eb a2 ff 2c 8f a6 70 d6 e6 31 41 6c b4 08 8f 23
00c0 4e 86 c6 c5 e4 23 af 5c bd d8 81 b9 b7 8d ff 63
00d0 c2 b3 ba 07 d3 22 b2 0d 88 df 98 55 9e 0c 2e ea
00e0 78 50 24 8b 39 1a ff 84 50 b1 c6 2d fe df c8 82
00f0 df 29 03 97 48 ee 83 5c 14 8a 05 f6 fe 8a 92 44
0100 1e 9d 23 a9 aa c3 b4 5c 8f 02 03 01 00 01
Certificate Extensions: 7
2.16.840.1.113730.1.13: Flags = 0, Length = 29
Netscape Comment
AC X509 Authority Generated Certificate
2.5.29.14: Flags = 0, Length = 16
Subject Key Identifier
8a5b294c6f7e29b3c5ed150186c2b89b89b76029
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=1dc996857ec8c8395029b1a19472aa8b11127972
2.5.29.31: Flags = 0, Length = 83
CRL Distribution Points
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://ca.asiacomtek.com/web.ca.asiacomtek.com.crl
[2]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://ca.asiacomtek.com/b-x509/crls/web.ca.asiacomtek.com.crl
2.5.29.19: Flags = 0, Length = 2
Basic Constraints
Subject Type=End Entity
Path Length Constraint=None
2.16.840.1.113730.1.1: Flags = 0, Length = 4
Netscape Cert Type
SSL Server Authentication (40)
2.5.29.17: Flags = 0, Length = 40
Subject Alternative Name
DNS Name=sapporo.lan.asiacomtek.com
DNS Name=admin.sapporo.lan.asiacomtek.com
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 4d 04 41 c2 eb ec b0 11 2b 2e af 68 88 40 b3 fb
0010 b8 65 76 e3 b8 db 9c 2b 45 32 40 c7 36 ad 5f 0d
0020 9a 32 c1 c8 da ae c4 5d c2 0a f1 3a 6e 1e d8 6e
0030 35 5b d0 a7 b8 34 fe a3 9c e7 8d f7 81 41 6f 3c
0040 d7 68 27 3b 94 94 bd 69 2f 2c a7 12 d6 79 b0 b4
0050 1e ad 0f 83 db bd 42 fb 75 97 a7 dd 05 6d 13 e7
0060 ef a7 46 46 a2 74 4c 49 64 5f 56 21 c4 95 f7 0e
0070 55 cf e6 78 39 de 95 b1 19 db 84 bc 20 0e 20 60
0080 17 59 58 79 f1 8b cf 99 de b5 e6 9f d2 c2 6b af
0090 fa b1 40 f7 a7 e7 37 b7 a6 44 ab 62 bc 98 c1 ea
00a0 5d 1e 59 e4 74 ad b6 03 79 f2 06 02 62 9c 9a ff
00b0 d4 66 ef 99 59 fc c0 ff db dd 7d ee a1 4e 2a 4f
00c0 28 1c d9 d3 45 4b e1 24 a1 41 02 9b 2b 6f 07 cf
00d0 4d c8 e7 4e fa 4f 80 9c 91 4b a3 71 9a 62 75 af
00e0 90 5b 1d 65 c6 b5 81 68 45 38 3a 0f b4 b7 9d d7
00f0 f3 31 0d b0 fd 0e 9c 72 47 f0 34 97 ee ce 78 8a
Non-root Certificate
Key Id Hash(rfc-sha1): 8a5b294c6f7e29b3c5ed150186c2b89b89b76029
Key Id Hash(sha1): 89fc2ac586acdaf3f9062a49b205cb2394290bdb
Key Id Hash(bcrypt-sha1): 913578726f7eaaa80e1db68e29103c7cbdae414d
Key Id Hash(bcrypt-sha256): 058b330fd758be7e7e122a2d159dba4911e48319caad7d0ba3caa0b24a6be777
Key Id Hash(md5): c093c8e5be30a6d2450ce04550567a7a
Key Id Hash(sha256): 11f682a855b9d9e6e621b28189d29a37520c98addc553911ce2bf5146c968336
Key Id Hash(pin-sha256): paZoXBLwSUrKNE++A+L9yqrN7jGwDcjHObdHrb+HILg=
Key Id Hash(pin-sha256-hex): a5a6685c12f0494aca344fbe03e2fdcaaacdee31b00dc8c739b747adbf8720b8
Cert Hash(md5): e024e2c91fc38017e328da41e420e440
Cert Hash(sha1): 9e9a4eee0596b1adfe9fa6f2cdc50e7b212260d5
Cert Hash(sha256): 79b209e1f90d3bc02baf914a769152aebb920abe2735577f9d9a5de5d0279dfd
Signature Hash: 917eb440fe12f92b94646165fd52964566547c883446353cf5f091d91bcdcd90
---------------- End Nesting Level 1 ----------------
CERT_KEY_IDENTIFIER_PROP_ID(20):
8a5b294c6f7e29b3c5ed150186c2b89b89b76029
CERT_MD5_HASH_PROP_ID(4):
e024e2c91fc38017e328da41e420e440
CERT_SHA1_HASH_PROP_ID(3):
9e9a4eee0596b1adfe9fa6f2cdc50e7b212260d5
CERT_KEY_CONTEXT_PROP_ID(5):
hCryptProv = 000002187E8E3710
KeySpec = 1 -- AT_KEYEXCHANGE
CERT_FRIENDLY_NAME_PROP_ID(11):
tomcat
CERT_ACCESS_STATE_PROP_ID(14):
AccessState = 0
Provider = Microsoft Enhanced Cryptographic Provider v1.0
ProviderType = 1
RSA
PP_KEYSTORAGE = 1
CRYPT_SEC_DESCR -- 1
KP_PERMISSIONS = 3f (63)
CRYPT_ENCRYPT -- 1
CRYPT_DECRYPT -- 2
CRYPT_EXPORT -- 4
CRYPT_READ -- 8
CRYPT_WRITE -- 10 (16)
CRYPT_MAC -- 20 (32)
D:(A;OICIID;GAGR;;;SY)(A;OICIID;GAGR;;;BA)(A;OICIID;GAGR;;;S-1-5-21-1313636688-3804510468-3646326021-1001)
Allow Full Control NT AUTHORITY\SYSTEM
Allow Full Control BUILTIN\Administrators
Allow Full Control JOEY-PC\Joey
Private Key:
PRIVATEKEYBLOB
Version: 2
aiKeyAlg: 0xa400
CALG_RSA_KEYX
Algorithm Class: 0xa000(5) ALG_CLASS_KEY_EXCHANGE
Algorithm Type: 0x400(2) ALG_TYPE_RSA
Algorithm Sub-id: 0x0(0) ALG_SID_RSA_ANY
0000 52 53 41 32 RSA2
0000 ...
048c
Encryption test passed
CertUtil: -dump command completed successfully.
JKS
Investigating Java Keystore files will require a valid installation of Java. Java installations are not as ubiquitous for Windows hosts as they are ffor UNIX hosts. For this reason, the example below shows the command being run from a Delphix Toolkit directory. Delphix provide a static Java deployment by default for each Environment user on a connected host and this deployment can be used to investigate certificates. Obviously, your own installation path (and certainly the UUID in the Delphix_COMMON directory) may differ.
> keytool <FILENAME> -list -v
Example
> "C:\Program Files\Delphix\DelphixConnector\Delphix_COMMON_0c9fb43e8eb1_host\java\jdk\bin\keytool" myKeystore.jks -list -v Enter keystore password: Keystore type: jks Keystore provider: SUN Your keystore contains 1 entry Alias name: tomcat Creation date: 08-Nov-2023 Entry type: PrivateKeyEntry Certificate chain length: 3 Certificate[1]: Owner: CN=sapporo, L=Sapporo, OU=Security, O=Delphix, ST=Hokkaido, C=JA Issuer: EMAILADDRESS=noreply@delphix.com, CN=web.ca.Delphix.com, L=Sapporo, OU=Security, O=Delphix, ST=Hokkaido, C=JA Serial number: 989681 Valid from: Fri May 28 01:59:40 UTC 2021 until: Thu Jul 16 01:59:40 UTC 2026 Certificate fingerprints: MD5: E0:24:E2:C9:1F:C3:80:17:E3:28:DA:41:E4:20:E4:40 SHA1: 9E:9A:4E:EE:05:96:B1:AD:FE:9F:A6:F2:CD:C5:0E:7B:21:22:60:D5 SHA256: 79:B2:09:E1:F9:0D:3B:C0:2B:AF:91:4A:76:91:52:AE:BB:92:0A:BE:27:35:57:7F:9D:9A:5D:E5:D0:27:9D:FD Signature algorithm name: SHA256withRSA Subject Public Key Algorithm: 2048-bit RSA key Version: 3 Extensions: #1: ObjectId: 2.16.840.1.113730.1.13 Criticality=false 0000: 16 27 41 43 20 58 35 30 39 20 41 75 74 68 6F 72 .'AC X509 Author 0010: 69 74 79 20 47 65 6E 65 72 61 74 65 64 20 43 65 ity Generated Ce 0020: 72 74 69 66 69 63 61 74 65 rtificate #2: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: 1D C9 96 85 7E C8 C8 39 50 29 B1 A1 94 72 AA 8B .......9P)...r.. 0010: 11 12 79 72 ..yr ] ] #3: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:[ CA:false PathLen: undefined ] #4: ObjectId: 2.5.29.31 Criticality=false CRLDistributionPoints [ [DistributionPoint: [URIName: http://ca.Delphix.com/web.ca.Delphix.com.crl] , DistributionPoint: [URIName: http://ca.Delphix.com/b-x509/crls/web.ca.Delphix.com.crl] ]] #5: ObjectId: 2.16.840.1.113730.1.1 Criticality=false NetscapeCertType [ SSL server ] #6: ObjectId: 2.5.29.17 Criticality=false SubjectAlternativeName [ DNSName: sapporo.lan.Delphix.com DNSName: admin.sapporo.lan.Delphix.com ] #7: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 8A 5B 29 4C 6F 7E 29 B3 C5 ED 15 01 86 C2 B8 9B .[)Lo.)......... 0010: 89 B7 60 29 ..`) ] ] Certificate[2]: Owner: EMAILADDRESS=noreply@delphix.com, CN=web.ca.Delphix.com, L=Sapporo, OU=Security, O=Delphix, ST=Hokkaido, C=JA Issuer: EMAILADDRESS=noreply@delphix.com, CN=root.ca.Delphix.com, OU=Security, O=Delphix, L=Sapporo, ST=Hokkaido, C=JA Serial number: 989680 Valid from: Thu May 27 07:31:17 UTC 2021 until: Sun May 25 07:31:17 UTC 2031 Certificate fingerprints: MD5: F4:F6:05:B5:32:A8:87:D9:CD:AC:4F:0A:F9:47:7C:DB SHA1: 22:8B:78:C6:1D:92:1F:2A:CB:4E:C2:3E:6D:47:5A:2C:B7:4D:90:E6 SHA256: 3F:16:1E:90:F1:17:C4:1F:4A:75:C6:92:6B:A1:9C:E1:58:D1:72:0E:7E:47:37:01:1A:9E:E5:E0:8A:7E:A5:A4 Signature algorithm name: SHA256withRSA Subject Public Key Algorithm: 2048-bit RSA key Version: 3 Extensions: #1: ObjectId: 2.16.840.1.113730.1.13 Criticality=false 0000: 16 27 41 43 20 58 35 30 39 20 41 75 74 68 6F 72 .'AC X509 Author 0010: 69 74 79 20 47 65 6E 65 72 61 74 65 64 20 43 65 ity Generated Ce 0020: 72 74 69 66 69 63 61 74 65 rtificate #2: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: 66 BA F8 37 0D 64 9C 61 A2 CE 5E FB 17 1F 13 5B f..7.d.a..^....[ 0010: 1F 06 79 46 ..yF ] ] #3: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:[ CA:true PathLen:2147483647 ] #4: ObjectId: 2.5.29.31 Criticality=false CRLDistributionPoints [ [DistributionPoint: [URIName: http://ca.Delphix.com/root.ca.Delphix.com.crl] , DistributionPoint: [URIName: http://ca.Delphix.com/b-x509/crls/root.ca.Delphix.com.crl] ]] #5: ObjectId: 2.16.840.1.113730.1.1 Criticality=false NetscapeCertType [ SSL server Object Signing ] #6: ObjectId: 2.5.29.17 Criticality=false SubjectAlternativeName [ DNSName: web.ca.Delphix.com ] #7: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 1D C9 96 85 7E C8 C8 39 50 29 B1 A1 94 72 AA 8B .......9P)...r.. 0010: 11 12 79 72 ..yr ] ] Certificate[3]: Owner: EMAILADDRESS=noreply@delphix.com, CN=root.ca.Delphix.com, OU=Security, O=Delphix, L=Sapporo, ST=Hokkaido, C=JA Issuer: EMAILADDRESS=noreply@delphix.com, CN=root.ca.Delphix.com, OU=Security, O=Delphix, L=Sapporo, ST=Hokkaido, C=JA Serial number: 15cc639928e61353272811a02361b88fd62affc7 Valid from: Thu May 27 07:27:12 UTC 2021 until: Fri May 23 07:27:12 UTC 2036 Certificate fingerprints: MD5: 3B:A3:2D:11:A6:BD:32:A6:AC:EF:D4:AD:AC:A1:17:30 SHA1: 0D:1E:48:DE:B0:1B:07:EA:84:C6:8E:92:63:A6:A4:4B:68:75:F5:45 SHA256: 92:C8:EB:2B:DE:0E:4C:0B:B1:F1:DE:07:82:46:78:CA:6A:61:49:48:43:94:37:BF:08:AC:1A:16:32:26:69:D5 Signature algorithm name: SHA256withRSA Subject Public Key Algorithm: 2048-bit RSA key Version: 3 Extensions: #1: ObjectId: 2.16.840.1.113730.1.13 Criticality=false 0000: 16 27 41 43 20 58 35 30 39 20 41 75 74 68 6F 72 .'AC X509 Author 0010: 69 74 79 20 47 65 6E 65 72 61 74 65 64 20 43 65 ity Generated Ce 0020: 72 74 69 66 69 63 61 74 65 rtificate #2: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: 66 BA F8 37 0D 64 9C 61 A2 CE 5E FB 17 1F 13 5B f..7.d.a..^....[ 0010: 1F 06 79 46 ..yF ] ] #3: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:[ CA:true PathLen:2147483647 ] #4: ObjectId: 2.5.29.31 Criticality=false CRLDistributionPoints [ [DistributionPoint: [URIName: http://ca.Delphix.com/root.ca.Delphix.com.crl] , DistributionPoint: [URIName: http://ca.Delphix.com/b-x509/crls/root.ca.Delphix.com.crl] ]] #5: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 66 BA F8 37 0D 64 9C 61 A2 CE 5E FB 17 1F 13 5B f..7.d.a..^....[ 0010: 1F 06 79 46 ..yF ] ] ******************************************* *******************************************
Related Articles
The following articles may provide more information or related information to this article:
