TB115 Delphix Plugin for Jenkins: TLS/SSL Certificate Validation Cannot Be Re-enabled Once Disabled
Alert Type
Security
Impact
Severity (NVD): Medium
Delphix CVSS v3.1 Score: CVSS Base Score: 5.9, Environmental Score: 5.4
Delphix CVSS v3.1 Vector: AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:L/A:N/MAV:A
Attack Vector (AV): Network [Modified Attack Vector (MAV): Adjacent]
Attack Complexity (AC): H
Privileges Required (PR): N
User Interaction (UI): R
Scope (S): U
Confidentiality (C): H
Integrity (I): L
Availability (A): N
By default, the Delphix Plugin for Jenkins validates that the TLS/SSL certificate for Delphix Control Tower (DCT) is valid and trusted. The plugin allows for this validation to be disabled by selecting the “Disable SSL Certificate Validation” checkbox for testing and troubleshooting. However, once disabled, this validation cannot be successfully re-enabled by deselecting the “Disable SSL Certificate Validation” checkbox, even though the plugin interface shows enabled.
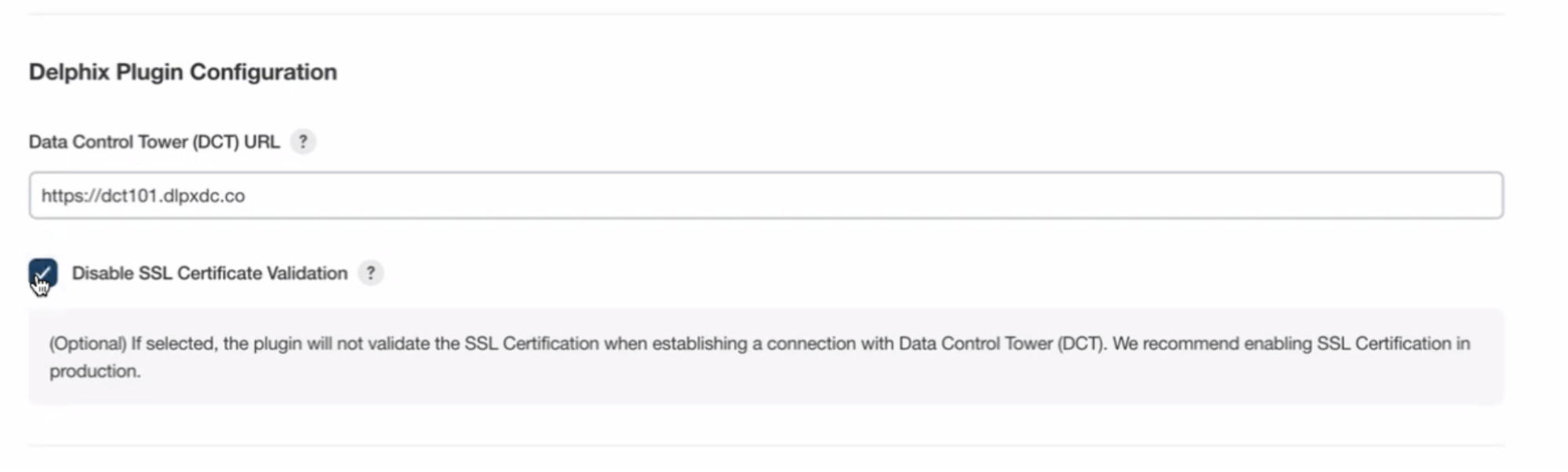
Illustration of the “Disable SSL Certificate Validation” check box with TLS/SSL certificate validation in the disabled state.
Disabling validation of TLS/SSL certificates is insecure and may allow a malicious agent to compromise the security of the network connection between a Jenkins server and DCT. This could expose DCT credential information that would otherwise be safeguarded by TLS. Exposed DCT credentials could be used to conduct privileged operations on Delphix Engines, environments, and data sources connected to DCT.
This vulnerability is only exploitable if a Jenkins administrator has disabled and then re-enabled the “Disable SSL Certificate Validation” checkbox, and if a malicious actor has successfully executed an interception (i.e. man-in-the-middle) attack to achieve network placement between the Delphix Plugin for Jenkins and DCT.
Affected Products and Versions
Delphix Plugin for Jenkins versions 3.0.1, 3.0.2, 3.0.3, and 3.1.0.
Symptoms
De-selecting the “Disable SSL Certificate Validation” checkbox will continue to ignore TLS/SSL certificate validation despite the enabled configuration in the Settings interface.
Relief/Workaround
The suggested path is to upgrade Delphix Plugin for Jenkins version 3.1.1, which will be available by February 23, 2024.
Otherwise, if customers are unable to upgrade to a later version, then uninstall and reinstall the presently installed Delphix Plugin for Jenkins version. This process will restore the default configuration where TLS/SSL certificate validation is enabled. In addition, as a precautionary measure customers may choose to rotate the DCT API Key used by the Delphix Plugin for Jenkins by deleting the old API Key and creating a new one. If the “Disable SSL Certificate Validation” is enabled again, then these workaround steps should be repeated.
Mitigation
Network security monitoring tools can be used to continuously scan the network for malicious attack vectors or abnormal behavior.
Inform Jenkins administrators who have access to the “Disable SSL Certification Validation” checkbox that they should not modify its value.
Resolution
This issue is resolved in the Delphix Plugin for Jenkins version 3.1.1 where the checkbox responds appropriately to input.
