How to Grant Non-Admin User Access to Object(s) in a Replication Namespace via CLI (KBA1670)
KBA
KBA#1670Overview
The Delphix Replication feature allows for Provisioning from Replicated Data Sources and VDBs. This allows a user to select an object (Data Source or virtaul database (VDB)) that resides on the replication target Engine, in the replication target namespace, as a source for a provision operation. By default, only an 'admin' user defined in Delphix can access the objects in the replication namespace. A non-admin user will not be able to see the namespace itself, or any of the objects in that namespace. This document will detail how to provide authorizations for a non-admin user to access the objects in the replication namespace for the purposes of provisioning.
Configuration and Requirements
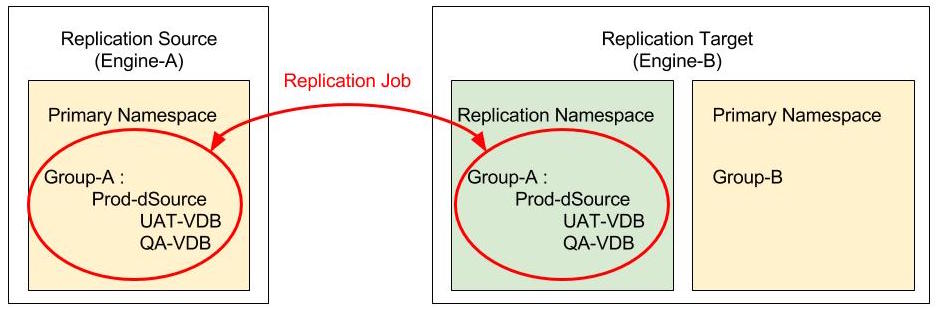
Given the above pre-existing configuration with the following pre-requirements:
- Non-Admin User (joe) - A non-admin Delphix user has been created on the replication target engine.
- Admin User (delphix_admin) - An admin user that can be used to set the authorizations for the non-admin user.
- Group (Group-B) - A group must exist in the primary namespace. This is the group into which the non-admin user wishes to provision a VDB>
- Replication Namespace (repl_source.domain) - Access to a replication target engine (Engine-B) that has an existing replication namespace that was created by running a replication job. Commonly, the replication namespace name is the name, or IP address, of the replication source Delphix Engine.
The following ‘authorizations' are required to be able to provision from objects in the replication namespace to the Primary Namespace (in Group-B):
-
‘Read’ privilege on the replication namespace - repl_source.domain
-
‘OWNER’ privilege on the group in the primary namespace - Group-B
-
One of the following:
-
‘PROVISIONER’ privilege on the entire group in the replication namespace. This allows the non-admin user to provision from any object in the specified group. Group-A and repl_source.domain
-
‘Read’ privilege on the group in the replication namespace AND ‘PROVISIONER’ privilege on the specific object(s) under that group. This allows the non-admin user to 'read', or view, all the objects in the specified group, but only provision from the specific object that was granted with the 'PROVISIONER' privilege. Group-A and Prod-dSource and repl_source.domain
-
Step 1: Connect to the Replication Target
As of Delphix version 5.1 the required authorizations cannot be granted using the GUI. The CLI must be used to provide the required authorizations. To access the CLI connect to the Delphix Engine via SSH as the admin user (delphix_admin):
Systems-MacBook-Pro:~ bk$ ssh -l delphix_admin Engine-B Password: <enter delphix_admin password> Engine-B>
Step 2: Get the replication namespace name and group name
Engine-B> cd /namespace Engine-B namespace> ls Objects NAME repl_source.domain
Engine-B> cd /group Engine-B group> ls Objects NAME DESCRIPTION Untitled Default Group RAC ORACLE Group-B
Step 3: List the current 'authorizations'
Engine-B> cd /authorization Engine-B authorization> ls Objects REFERENCE USER ROLE TARGET AUTHORIZATION-1 sysadmin OWNER sysadmin AUTHORIZATION-2 delphix_admin OWNER delphix_admin AUTHORIZATION-3 delphix_admin OWNER domain0 AUTHORIZATION-35 joe OWNER joe
Step 4: Set 'OWNER' privilege on group in primary namespace
Engine-B authorization> create Engine-B authorization create *> set user=joe Engine-B authorization create *> set role=OWNER Engine-B authorization create *> set target=Group-B Engine-B authorization create *> commit Engine-B authorization> ls Objects REFERENCE USER ROLE TARGET AUTHORIZATION-1 sysadmin OWNER sysadmin AUTHORIZATION-2 delphix_admin OWNER delphix_admin AUTHORIZATION-3 delphix_admin OWNER domain0 AUTHORIZATION-35 joe OWNER joe AUTHORIZATION-58 joe OWNER Group:/Group-B
Step 5: Set 'Read' privilege on the replication namespace
Engine-B authorization> create Engine-B authorization create *> set user=joe Engine-B authorization create *> set role=Read Engine-B authorization create *> set target=Namespace:/repl_source.domain Engine-B authorization create *> commit Engine-B authorization> ls Objects REFERENCE USER ROLE TARGET AUTHORIZATION-1 sysadmin OWNER sysadmin AUTHORIZATION-2 delphix_admin OWNER delphix_admin AUTHORIZATION-3 delphix_admin OWNER domain0 AUTHORIZATION-35 joe OWNER joe AUTHORIZATION-58 joe OWNER Group-B AUTHORIZATION-60 joe Read Namespace:repl_source.domain
Step 6: Set 'PROVISIONER' privilege on the group/object to provision from
The following are examples of how to set the 'PROVISIONER' privilege on the required object(s) based on the level of authorization required. More general access is provided by granting this privilege to all objects in the group, or more specific access is provided by granting privilege to only specific object within a group.
Example 1: Set 'PROVISIONER' for the entire group in the replication namespace. This will allow the non-admin user (joe) to provision from any object in that group (Group-A):
Engine-B authorization> create Engine-B authorization create *> set user=joe Engine-B authorization create *> set role=PROVISIONER Engine-B authorization create *> set target=Group-A@repl_source.domain Engine-B authorization create *> commit Engine-B authorization> ls Objects REFERENCE USER ROLE TARGET AUTHORIZATION-1 sysadmin OWNER sysadmin AUTHORIZATION-2 delphix_admin OWNER delphix_admin AUTHORIZATION-3 delphix_admin OWNER domain0 AUTHORIZATION-35 joe OWNER joe AUTHORIZATION-58 joe OWNER Group-B AUTHORIZATION-60 joe Read repl_source.domain AUTHORIZATION-61 joe PROVISIONER Group-A@repl_source.domain
Example 2: Set 'PROVISIONER' for only a specific object (Prod-dSource) in a specific group (Group-A). This allows the non-admin user (joe) to be able to 'read', or view, all the objects in a group (Group-A), but only provision from a specific object (Prod-dSource).
Engine-B authorization> create Engine-B authorization create *> set user=joe Engine-B authorization create *> set role=Read Engine-B authorization create *> set target=Group-A@repl_source.domain Engine-B authorization create *> commit Engine-B authorization> create Engine-B authorization create *> set user=joe Engine-B authorization create *> set role=PROVISIONER Engine-B authorization create *> set target=Group-A@repl_source.domain/Prod-dSource@repl_source.domain Engine-B authorization create *> commit Engine-B authorization> ls Objects REFERENCE USER ROLE TARGET AUTHORIZATION-1 sysadmin OWNER sysadmin AUTHORIZATION-2 delphix_admin OWNER delphix_admin AUTHORIZATION-3 delphix_admin OWNER domain0 AUTHORIZATION-35 joe OWNER joe AUTHORIZATION-58 joe OWNER Group-B AUTHORIZATION-60 joe Read repl_source.domain AUTHORIZATION-62 joe Read Group-A@repl_source.domain AUTHORIZATION-63 joe PROVISIONER Group-A@repl_source.domain/Prod-dSource@repl_source.domain
Step 7: Log into the Delphix Engine UI as the non-admin user
After logging into the Delphix Engine UI as the non-admin user the namespace and applicable objects from that namespace will be accessible.
CLI NOTE: The CLI supports <tab completion> to assist in fining available options for properties. In the following example, when specifying the target property for a specific authorization the user started typing the group name, Group-A, then hit the <tab key> and the CLI provided a list of available substitutions:
Engine-B authorization> create Engine-B authorization create *> set user=joe Engine-B authorization create *> set role=Read Engine-B authorization create *> set target=Group-A<tab key> Group-A@repl_source.domain Group-A@repl_source.domain/UAT-VDB@repl_source.domain Group-A@repl_source.domain/QA-VDB@repl_source.domain Group-A@repl_source.domain/Prod-dSource@repl_source.domain Engine-B authorization create *> set target=Group-A@repl_source.domain Engine-B authorization create *> commit
